Report finds that many critical infrastructure networks can be breached using simple attacks. Plus, a new MITRE Engenuity tool uses machine learning to infer attack sequences. Meanwhile, CISA will lead a project to standardize civilian agencies’ cyber operations. And get the latest on XSS vulnerabilities, CIS Benchmarks and a China-backed botnet’s takedown!
Dive into six things that are top of mind for the week ending September 20.
1 - CISA: Critical infrastructure orgs susceptible to common attacks
After assessing the security of 143 critical infrastructure organizations in 2023, the U.S. government found most of the networks could be breached using ordinary, well-known attack methods.
That’s according to “CISA Analysis: Fiscal Year 2023 Risk and Vulnerability Assessments,” a report about the risk and vulnerability assessments (RVAs) conducted by the Cybersecurity and Infrastructure Security Agency (CISA) and the U.S. Coast Guard (USCG).
Specifically, CISA and USCG assessors had the most success gaining initial access, attaining network permanence, evading defenses and moving laterally by using valid accounts, phishing schemes and default credentials – all simple attack methods.
For example, the use of valid accounts, which are legitimate accounts whose login credentials have been compromised, was the most successful attack technique for achieving:
- Initial access (41.3%)
- Persistence (42.2%)
- Privilege escalation (44.7%)
Valid-account use also ranked as the second most successful attack technique for evading defenses.
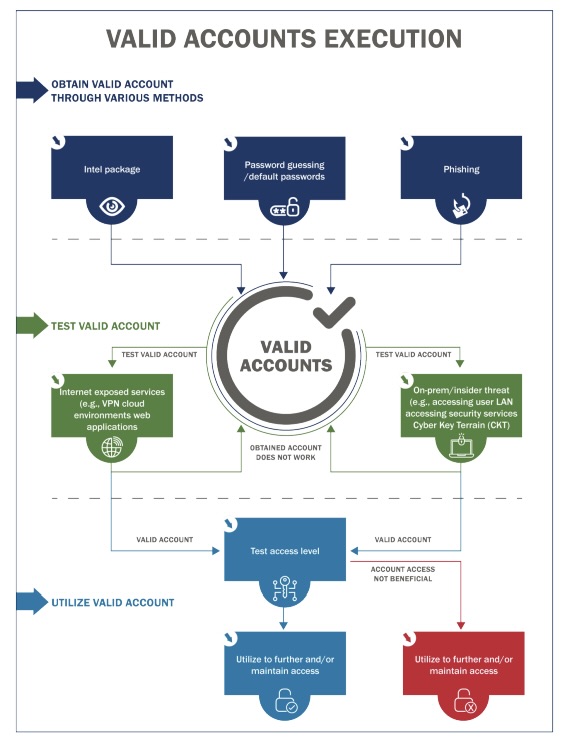
(Source: “CISA Analysis: Fiscal Year 2023 Risk and Vulnerability Assessments” report, September 2024)
The report offers troves of recommendations to critical infrastructure organizations, including:
- Adopt a secure password policy that requires phishing-resistant multi-factor authentication for remote access; strong passwords; unique credentials, and more.
- Maintain a comprehensive asset inventory, and keep software updated and patched.
- Segment networks and block outbound connections from internet-facing servers to prevent lateral movement and privilege escalation.
Each of the 143 critical infrastructure organizations received a report about their network security results, mapped to the MITRE ATT&CK framework. Each report included key findings, improvement recommendations, potential mitigations and attack path details.
To get more details, read the 24-page “CISA Analysis: Fiscal Year 2023 Risk and Vulnerability Assessments” report and complementary charts.
For more information about protecting critical infrastructure environments and about operational technology (OT) security, check out these Tenable resources:
- “Critical Infrastructure Cybersecurity: Disrupt OT Attack Vectors in the New Era of Distrust” (white paper)
- “Addressing Critical Infrastructure Threats for State and Local Governments” (solution overview)
- “CISA Finding: 90% of Initial Access to Critical Infrastructure Is Gained Via Identity Compromise. What Can You Do About It?” (blog)
- “Enhancing Critical Infrastructure Cybersecurity for Water Utilities” (infographic)
- “Adhering to the NIST Framework with Tenable OT Security” (data sheet)
2 - New MITRE tool uses ML to anticipate cyberattacks
To help cybersecurity teams stay ahead of hackers, MITRE Engenuity has released a new browser-based tool designed to predict cyberattack sequences.
The Technique Inference Engine (TIE) lets cybersecurity pros input tactics or techniques from the MITRE ATT&CK knowledge base they’ve detected in their environment. Using a machine learning (ML) model, TIE then infers the following steps that attackers would most likely take.
“TIE will help analysts quickly understand what is likely to have happened next, based on a broad corpus of threat intelligence,” reads a MITRE Engenuity blog about the new tool.
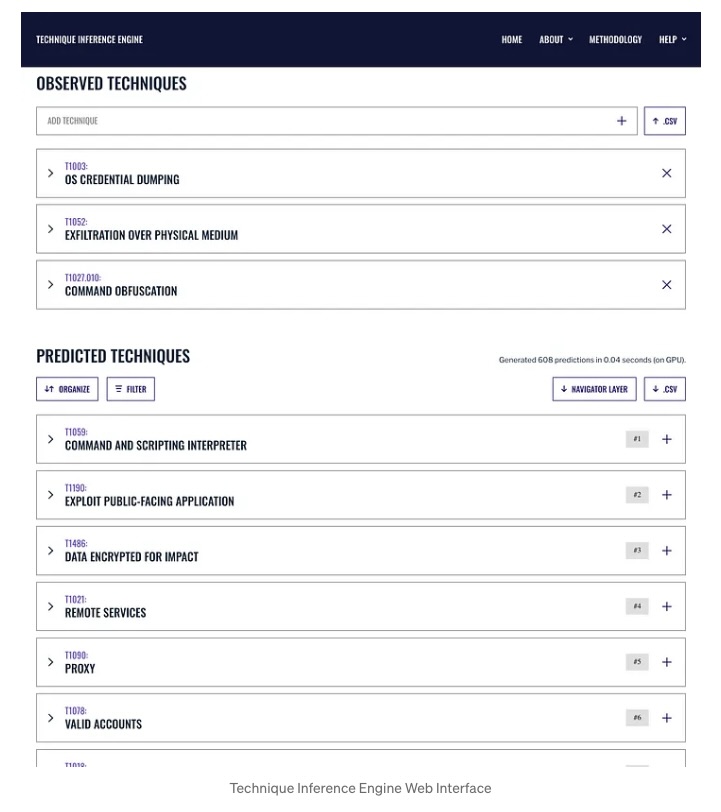
(Source: MITRE Engenuity, September 2024)
With the TIE results in hand, cybersecurity teams can, among other things, do the following:
- Prioritize techniques to look for while triaging an event.
- Improve post-mortem incident analysis by highlighting potential gaps.
- Help create adversary emulation plans.
“We’re delighted to provide the community with a tool that gives defenders a way to identify what you don’t detect,” the blog reads
MITRE Engenuity built TIE in collaboration with experts from nine other organizations, including Tenable Research.
“Tenable Research is proud to be a key contributor to the new MITRE Engenuity Technique Inference Engine (TIE) – a powerful resource for security teams. TIE leverages machine learning to predict adversarial behaviors based on real-world cyber threat intelligence, helping you stay one step ahead of attackers,” reads a Tenable LinkedIn post.
To get more details, check out:
- The blog “Know your Adversary’s next move with TIE”
- The Technique Inference Engine’s web interface
- The TIE project’s home page
- The TIE’s GitHub page
3 - CISA: Fed agencies must adopt a common security posture
Is your company considering implementing a consistent and uniform set of foundational cybersecurity practices for all teams and departments throughout the organization? If so, you might want to check out how the U.S. government plans to do just that across 100-plus federal agencies.
CISA will be in charge of the project, which it detailed in the document “Federal Civilian Executive Branch (FCEB) Operational Cybersecurity Alignment (FOCAL) Plan,” announced this week.
The goal: To standardize the cybersecurity operations of civilian agencies in the executive branch, known by the acronym FCEB, to ensure they can all properly manage cyber risk in today’s complex and fast-evolving threat landscape.

Currently, these agencies architect their IT and cybersecurity operations independently, and consequently their ability to manage cyber risk varies. “There is no cohesive or consistent baseline security posture across all FCEB agencies” and as a result “the FCEB remains vulnerable,” CISA says in the FOCAL plan’s document.
“Collective operational defense is required to adequately reduce risk posed to more than 100 FCEB agencies and to address dynamic cyber threats to government services and data,” the plan’s document reads.
The FOCAL plan focuses on five core areas:
- Asset management
- Vulnerability management
- Defensible architecture
- Cyber supply-chain risk management
- Incident detection and response
“The FOCAL Plan was developed for FCEB agencies, but public and private sector organizations should find it useful as a roadmap to establish their own plan to bolster coordination of their enterprise security capabilities,” reads a CISA statement.
To get more details, check out:
- The plan’s announcement “CISA Releases Plan to Align Operational Cybersecurity Priorities for Federal Agencies”
- The FOCAL plan’s description
4 - FBI takes down China-controlled IoT botnet used to steal information
A botnet of 260,000-plus IoT devices used to conduct information-stealing attacks on behalf of China’s government against targets in the U.S. and abroad has been dismantled.
Working with international partners, the FBI led the operation against the botnet, which was active since 2021 and was controlled by Beijing-based IT contractor Integrity Technology Group, also known as Flax Typhoon.
Hackers working for Flax Typhoon created the botnet by breaching 260,000-plus consumer IoT devices in the U.S. and in other countries. By using these legitimate devices, the hackers made their attacks look like normal internet traffic.

Flax Typhoon developed an application that allowed the hackers to control the botnet’s compromised devices, while another tool offered them a menu of malicious commands.
The infected devices, which included small office / home office (SOHO) routers, IP cameras, digital video recorders and network-attached storage devices, got disconnected from the botnet as part of the FBI’s operation. The devices’ legitimate operations weren’t disrupted.
These are some FBI recommendations for preventing the hijacking of IoT devices for botnets, and for protecting networks from active botnets:
- Disable unused services and ports, such as remote management options and file sharing services.
- Segment networks and use the least-privilege principle to limit the risk from compromised IoT devices.
- Keep software and firmware patched and updated.
- Replace default passwords with strong passwords.
- Periodically reboot IoT devices, which terminates running processes and may remove some malware types.
- Replace end-of-life equipment with products that vendors are actively supporting.
To get more details, check out:
- The Department of Justice’s announcement “Court-Authorized Operation Disrupts Worldwide Botnet Used by People’s Republic of China State-Sponsored Hackers”
- The court warrant
- The FBI’s cybersecurity advisory “People’s Republic of China-Linked Actors Compromise Routers and IoT Devices for Botnet Operations”
For more information about IoT and OT security, check out these Tenable resources:
- “How To Secure All of Your Assets - IT, OT and IoT - With an Exposure Management Platform” (blog)
- “Discover, Measure, and Minimize the Risk Posed by Your Interconnected IT/OT/IoT Environments” (on-demand webinar)
- “Unlock Advanced IoT Visibility in your OT Environment Security” (on-demand webinar)
- “How to Tackle OT Challenges: Asset Inventory and Vulnerability Assessment” (blog)
- “Securing IT/OT Convergence for Industry 4.0 Success” (on-demand webinar)
5 - CISA issues plea to end XSS vulnerabilities
Although cross-site scripting (XSS) vulnerabilities are easily preventable, software makers continue introducing them into their products, a situation that needs to stop.
So said CISA and the FBI in the fact sheet “Secure by Design Alert: Eliminating Cross-Site Scripting Vulnerabilities.”
When software makers neglect to properly “validate, sanitize or escape inputs,” XSS vulnerabilities can crop up, allowing attackers to inject malicious scripts into web apps, according to the fact sheet.
“CISA and FBI urge CEOs and other business leaders at technology manufacturers to direct their technical leaders/teams to review past instances of these defects and create a strategic plan to prevent them in the future,” the fact sheet reads.

Recommendations for software makers to prevent XSS vulnerabilities include:
- Validate the structure and meaning of inputs
- Carry out code reviews
- Use output-encoding functions in modern web frameworks
- Conduct adversarial testing to assess the quality and security of code
For more information about XSS bugs:
- “What Is Cross-Site Scripting (XSS)?” (TechTarget)
- “Cross Site Scripting (XSS)” (OWASP)
- “Understanding the Threat of XSS” (IEEE Computer Society)
- “How to prevent XSS” (PortSwigger)
- “Cross Site Scripting Prevention Cheat Sheet” (OWASP)
6 - CIS publishes new, updated Benchmarks for Microsoft, Google and Apache products
Microsoft’s Windows Server OS. Google’s ChromeOS. Apache’s Cassandra database.
Those products are among the CIS Benchmarks that were either updated or newly released in August by the Center for Internet Security.
Specifically, these secure-configuration recommendations were updated in June:
- CIS Apache Cassandra 3.11 Benchmark v1.2.0
- CIS Apache Cassandra 4.0 Benchmark v1.1.0
- CIS Microsoft Windows Server 2016 STIG Benchmark v3.0.0

In addition, CIS released brand new Benchmarks for Apache’s Cassandra 4.1 and Tomcat 10.1; FreeBSD 14 Benchmark v1.0.0; Google’s ChromeOS; and Ubuntu Linux 24.04 LTS.
Organizations can use the CIS Benchmarks’ secure-configuration guidelines to harden products against attacks. Currently, there are more than 100 Benchmarks for 25-plus vendor product families in categories including:
- cloud platforms
- databases
- desktop and server software
- mobile devices
- operating systems
To get more details, read the CIS blog “CIS Benchmarks September 2024 Update.”
For more information about the CIS Benchmarks list, check out its home page, as well as:
- “Getting to Know the CIS Benchmarks” (CIS)
- “Security Via Consensus: Developing the CIS Benchmarks” (Dark Reading)
- “How to Unlock the Security Benefits of the CIS Benchmarks” (Tenable)
- “CIS Benchmarks Communities: Where configurations meet consensus” (Help Net Security)
- “CIS Benchmarks: DevOps Guide to Hardening the Cloud” (DevOps)

The post Cybersecurity Snapshot: Critical Infrastructure Orgs Found Vulnerable to Basic Hacks, While New MITRE Tool Uses ML to Predict Attack Chains appeared first on Security Boulevard.
Juan Perez
Source: Security Boulevard
Source Link: https://securityboulevard.com/2024/09/cybersecurity-snapshot-critical-infrastructure-orgs-found-vulnerable-to-basic-hacks-while-new-mitre-tool-uses-ml-to-predict-attack-chains/