Microsoft is publishing 55 vulnerabilities this February 2026 Patch Tuesday. Microsoft is aware of exploitation in the wild for six of today’s vulnerabilities, and notes public disclosure for three of those. Earlier in the month, Microsoft provided patches to address three browser vulnerabilities, which are not included in the Patch Tuesday count above.
Windows/Office triple trouble: zero-day security feature bypass vulns
All three of the publicly disclosed zero-day vulnerabilities published today are security feature bypasses, and Microsoft acknowledges the same cast of reporters in each case.
CVE-2026-21510 describes a zero-day Windows Shell security feature bypass vulnerability which is already exploited in the wild. Not to be confused with PowerShell, most people will use the Windows Shell without ever learning its name or even really contemplating its existence. The Windows Shell is Microsoft’s term for the GUI interaction logic for the entire OS provided by explorer.exe and associated libraries and APIs.
CVE-2026-21510 provides an attacker with a way to dodge those pesky Smart Screen or other “are you sure?” prompts. The advisory sets out that “an attacker must convince a user to open a malicious link or shortcut file”. We could parse this wording more than one way, and while shortcut files with a .lnk extension are certainly a prime suspect here, it’s possible that .url files might also be a vector.
The venerable MSHTML/Trident web rendering engine is still present in Windows as a daily driver for Office and Explorer, many years after most people stopped using Internet Explorer. Accordingly, every so often Microsoft has to patch another zero-day vulnerability in the browser it can’t quite bring itself to rip out of its flagship operating system. Today’s example is CVE-2026-21513, a security feature bypass which starts with the attacker convincing a user to open a malicious HTML file or shortcut file.
If good things come in threes, then perhaps CVE-2026-21514 makes security bypass zero-day vulnerabilities a good thing. Exploitation involves bypassing Object Linking & Embedding (OLE) mitigations by convincing the user to open a malicious Word document. The advisory only lists remediations for LTSC versions of Office and on-prem Microsoft 365 Apps for Enterprise, without mentioning the standard Microsoft 365 suite.
It’s curious that Microsoft has evaluated the attack vector for CVE-2026-21514 as local, because MSRC typically assesses any vulnerability which boils down to “remote attacker tricks user into opening malicious payload” as a remote attack, based on the location of the attacker. However, the advisory specifically calls out that “reliance on untrusted inputs in a security decision in Microsoft Office Word allows an unauthorized attacker to bypass a security feature locally.” It’s not clear whether this is a deviation from prior practice by MSRC, an inadvertent mis-assessment, or an unusual-but-correct assessment of an attack vector that relies on details which Microsoft has not made public. Happily, the Preview Pane is not a vector, which raises the bar slightly for an attacker, since the user must explicitly open the malicious file or web page.
Ultimately, although none of the advisories for CVE-2026-21510, CVE-2026-21513, or CVE-2026-21514 explicitly come out and say it, it’s likely that exploitation in each case involves tricking Windows into participating in another Mark-of the Web laundering scheme using flaws in old components.
Windows DWM: zero-day elevation of privilege
For the second month in a row, the Windows Desktop Windows Manager (DWM) is the site of an exploited-in-the-wild zero-day vulnerability. Last month’s CVE-2026-20805 was an information disclosure vulnerability, effectively a treasure map for threat actors seeking the otherwise obfuscated in-memory address of the kernel-space DWM process. The publication of zero-day elevation of privilege (EoP) vulnerability CVE-2026-21519 today very likely reflects MSTIC and MSRC working to thwart the same threat actor in both cases. As Rapid7 has noted in the past, initial access coupled with local elevation of privilege vulnerabilities is the staple diet of many successful attackers, so the lower CVSS v3 base score of 7.8 seen here versus a broadly equivalent remote code execution is not a sign to delay patching.
Remote Desktop Services: zero-day elevation of privilege
Remote Desktop Services (RDP) are designed to allow a duly authorized remote user to interact with the server, but CVE-2026-21533 allows an unauthorized local user to elevate privileges to SYSTEM. Every Windows Server product back as far as Server 2012 receives patches, so this one has been present for a while. It’s possible that today’s patches close off a long-running exploitation story for at least one threat actor.
RasMan: zero-day denial of service
Exploited in the wild, but perhaps of less concern is CVE-2026-21525, a local denial of service vulnerability in the Windows Remote Access Connection Manager (RasMan). Somewhat unusually for a local vulnerability, the advisory sets out that no privileges are required at all, so even a guest account can exploit this one. You have disabled those guest accounts, right?
Microsoft lifecycle update
There are no significant Microsoft product lifecycle changes this month.
Summary Charts
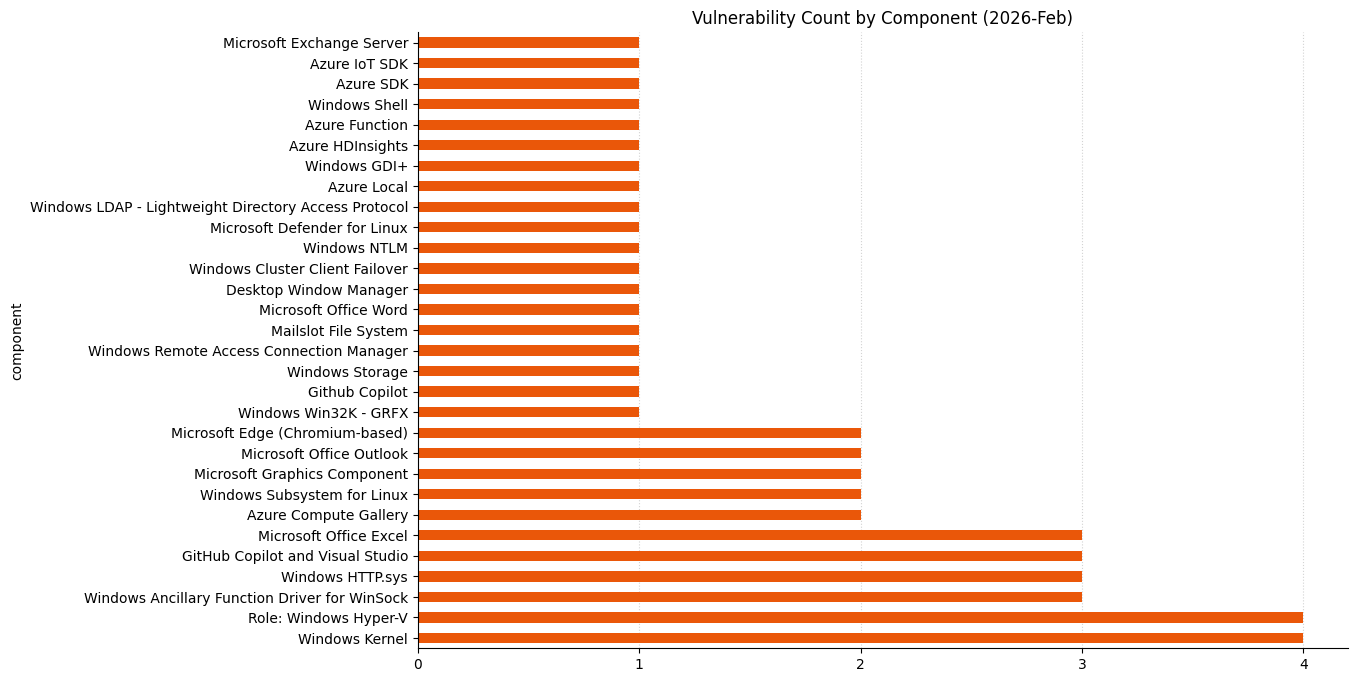
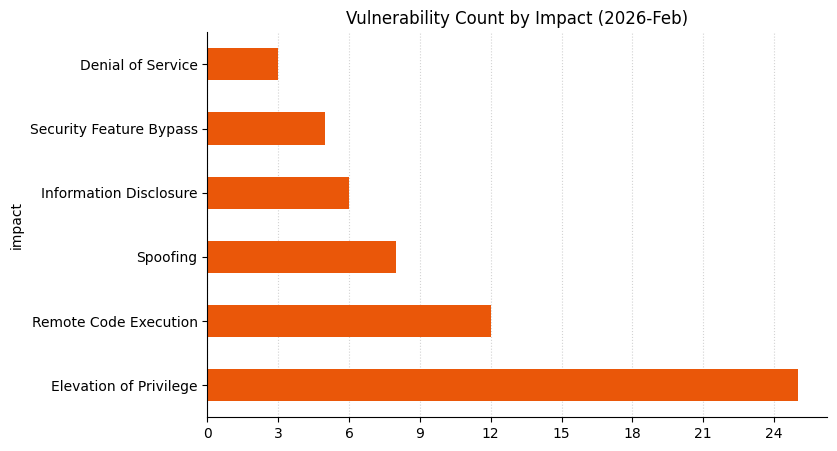
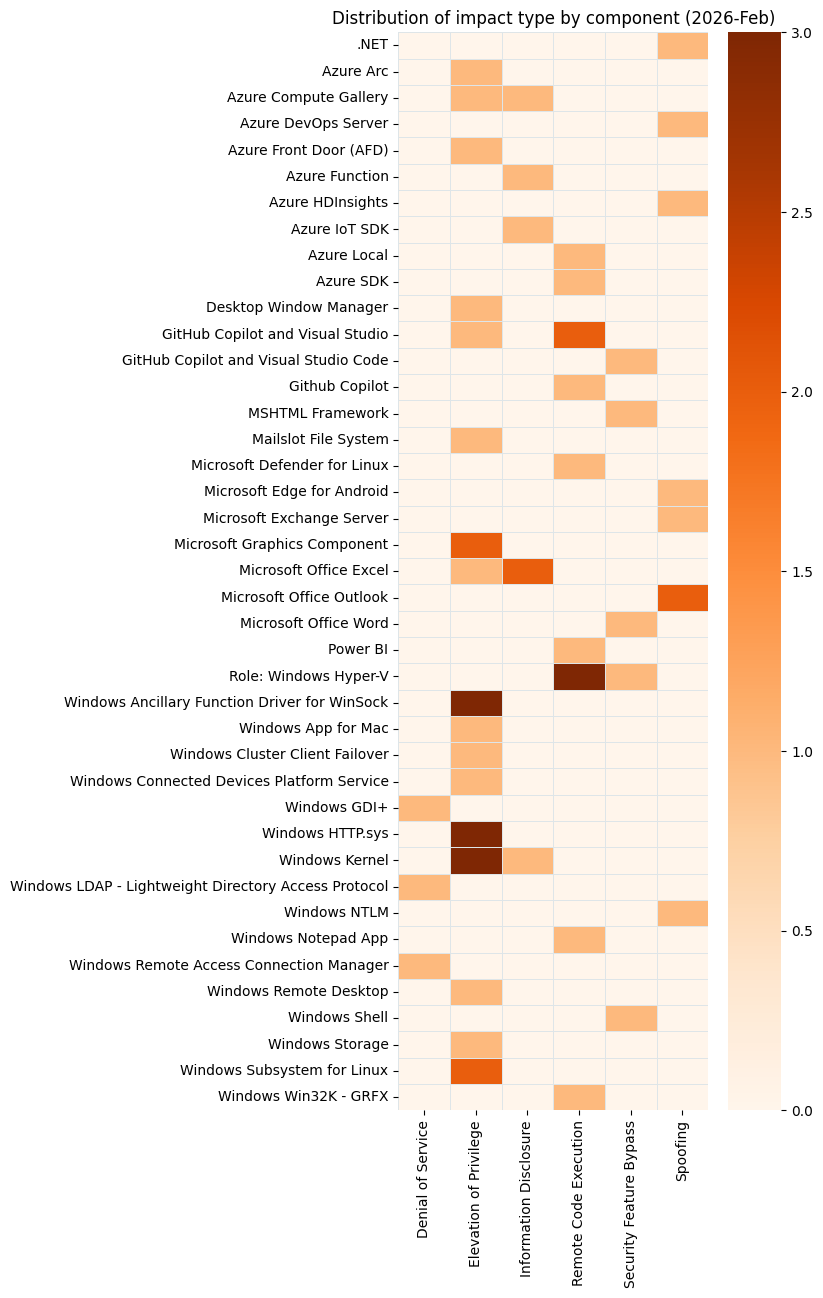
Summary Tables
Apps vulnerabilities
CVE | Title | Exploitation status | Publicly disclosed? | CVSS v3 base score |
|---|---|---|---|---|
| CVE-2026-20841 | Windows Notepad App Remote Code Execution Vulnerability | Exploitation Less Likely | No | 8.8 |
Azure vulnerabilities
CVE | Title | Exploitation status | Publicly disclosed? | CVSS v3 base score |
|---|---|---|---|---|
| CVE-2026-21512 | Azure DevOps Server Cross-Site Scripting Vulnerability | Exploitation Less Likely | No | 6.5 |
| CVE-2026-21529 | Azure HDInsight Spoofing Vulnerability | Exploitation Unlikely | No | 5.7 |
| CVE-2026-21528 | Azure IoT Explorer Information Disclosure Vulnerability | Exploitation Unlikely | No | 6.5 |
| CVE-2026-21228 | Azure Local Remote Code Execution Vulnerability | Exploitation Less Likely | No | 8.1 |
| CVE-2026-21531 | Azure SDK for Python Remote Code Execution Vulnerability | Exploitation Less Likely | No | 9.8 |
| CVE-2026-21522 | Microsoft ACI Confidential Containers Elevation of Privilege Vulnerability | Exploitation Less Likely | No | 6.7 |
| CVE-2026-23655 | Microsoft ACI Confidential Containers Information Disclosure Vulnerability | Exploitation Less Likely | No | 6.5 |
Developer Tools vulnerabilities
CVE | Title | Exploitation status | Publicly disclosed? | CVSS v3 base score |
|---|---|---|---|---|
| CVE-2026-21218 | .NET Spoofing Vulnerability | Exploitation Unlikely | No | 7.5 |
| CVE-2026-21523 | GitHub Copilot and Visual Studio Code Remote Code Execution Vulnerability | Exploitation Less Likely | No | 8.0 |
| CVE-2026-21518 | GitHub Copilot and Visual Studio Code Security Feature Bypass Vulnerability | Exploitation Less Likely | No | 6.5 |
| CVE-2026-21257 | GitHub Copilot and Visual Studio Elevation of Privilege Vulnerability | Exploitation Less Likely | No | 8.0 |
| CVE-2026-21256 | GitHub Copilot and Visual Studio Remote Code Execution Vulnerability | Exploitation Less Likely | No | 8.8 |
ESU vulnerabilities
CVE | Title | Exploitation status | Publicly disclosed? | CVSS v3 base score |
|---|---|---|---|---|
| CVE-2026-21519 | Desktop Window Manager Elevation of Privilege Vulnerability | Exploitation Detected | No | 7.8 |
| CVE-2026-20846 | GDI+ Denial of Service Vulnerability | Exploitation Less Likely | No | 7.5 |
| CVE-2026-21253 | Mailslot File System Elevation of Privilege Vulnerability | Exploitation More Likely | No | 7.0 |
| CVE-2026-21527 | Microsoft Exchange Server Spoofing Vulnerability | Exploitation Less Likely | No | 6.5 |
| CVE-2026-21513 | MSHTML Framework Security Feature Bypass Vulnerability | Exploitation Detected | Yes | 8.8 |
| CVE-2026-21236 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | Exploitation Unlikely | No | 7.8 |
| CVE-2026-21238 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | Exploitation More Likely | No | 7.8 |
| CVE-2026-21234 | Windows Connected Devices Platform Service Elevation of Privilege Vulnerability | Exploitation Unlikely | No | 7.0 |
| CVE-2026-21246 | Windows Graphics Component Elevation of Privilege Vulnerability | Exploitation Unlikely | No | 7.8 |
| CVE-2026-21235 | Windows Graphics Component Elevation of Privilege Vulnerability | Exploitation Less Likely | No | 7.3 |
| CVE-2026-21240 | Windows HTTP.sys Elevation of Privilege Vulnerability | Exploitation Less Likely | No | 7.8 |
| CVE-2026-21248 | Windows Hyper-V Remote Code Execution Vulnerability | Exploitation Less Likely | No | 7.3 |
| CVE-2026-21247 | Windows Hyper-V Remote Code Execution Vulnerability | Exploitation Less Likely | No | 7.3 |
| CVE-2026-21244 | Windows Hyper-V Remote Code Execution Vulnerability | Exploitation Less Likely | No | 7.3 |
| CVE-2026-21255 | Windows Hyper-V Security Feature Bypass Vulnerability | Exploitation Less Likely | No | 8.8 |
| CVE-2026-21239 | Windows Kernel Elevation of Privilege Vulnerability | Exploitation Less Likely | No | 7.8 |
| CVE-2026-21231 | Windows Kernel Elevation of Privilege Vulnerability | Exploitation More Likely | No | 7.8 |
| CVE-2026-21222 | Windows Kernel Information Disclosure Vulnerability | Exploitation Less Likely | No | 5.5 |
| CVE-2026-21249 | Windows NTLM Spoofing Vulnerability | Exploitation Less Likely | No | 3.3 |
| CVE-2026-21525 | Windows Remote Access Connection Manager Denial of Service Vulnerability | Exploitation Detected | No | 6.2 |
| CVE-2026-21533 | Windows Remote Desktop Services Elevation of Privilege Vulnerability | Exploitation Detected | No | 7.8 |
| CVE-2026-21510 | Windows Shell Security Feature Bypass Vulnerability | Exploitation Detected | Yes | 8.8 |
| CVE-2026-21508 | Windows Storage Elevation of Privilege Vulnerability | Exploitation Less Likely | No | 7.0 |
| CVE-2026-21242 | Windows Subsystem for Linux Elevation of Privilege Vulnerability | Exploitation Less Likely | No | 7.0 |
| CVE-2026-21237 | Windows Subsystem for Linux Elevation of Privilege Vulnerability | Exploitation Less Likely | No | 7.0 |
Microsoft Office vulnerabilities
CVE | Title | Exploitation status | Publicly disclosed? | CVSS v3 base score |
|---|---|---|---|---|
| CVE-2026-21259 | Microsoft Excel Elevation of Privilege Vulnerability | Exploitation Less Likely | No | 7.8 |
| CVE-2026-21258 | Microsoft Excel Information Disclosure Vulnerability | Exploitation Less Likely | No | 5.5 |
| CVE-2026-21261 | Microsoft Excel Information Disclosure Vulnerability | Exploitation Less Likely | No | 5.5 |
| CVE-2026-21260 | Microsoft Outlook Spoofing Vulnerability | Exploitation Unlikely | No | 7.5 |
| CVE-2026-21511 | Microsoft Outlook Spoofing Vulnerability | Exploitation More Likely | No | 7.5 |
| CVE-2026-21514 | Microsoft Word Security Feature Bypass Vulnerability | Exploitation Detected | Yes | 7.8 |
Other vulnerabilities
CVE | Title | Exploitation status | Publicly disclosed? | CVSS v3 base score |
|---|---|---|---|---|
| CVE-2026-21516 | GitHub Copilot for Jetbrains Remote Code Execution Vulnerability | Exploitation Less Likely | No | 8.8 |
Server Software vulnerabilities
CVE | Title | Exploitation status | Publicly disclosed? | CVSS v3 base score |
|---|---|---|---|---|
| CVE-2026-21527 | Microsoft Exchange Server Spoofing Vulnerability | Exploitation Less Likely | No | 6.5 |
SQL Server vulnerabilities
CVE | Title | Exploitation status | Publicly disclosed? | CVSS v3 base score |
|---|---|---|---|---|
| CVE-2026-21229 | Power BI Remote Code Execution Vulnerability | Exploitation Unlikely | No | 8.0 |
System Center vulnerabilities
CVE | Title | Exploitation status | Publicly disclosed? | CVSS v3 base score |
|---|---|---|---|---|
| CVE-2026-21537 | Microsoft Defender for Endpoint Linux Extension Remote Code Execution Vulnerability | Exploitation Less Likely | No | 8.8 |
Windows vulnerabilities
CVE | Title | Exploitation status | Publicly disclosed? | CVSS v3 base score |
|---|---|---|---|---|
| CVE-2026-21251 | Cluster Client Failover (CCF) Elevation of Privilege Vulnerability | Exploitation Unlikely | No | 7.8 |
| CVE-2026-21519 | Desktop Window Manager Elevation of Privilege Vulnerability | Exploitation Detected | No | 7.8 |
| CVE-2026-20846 | GDI+ Denial of Service Vulnerability | Exploitation Less Likely | No | 7.5 |
| CVE-2026-21253 | Mailslot File System Elevation of Privilege Vulnerability | Exploitation More Likely | No | 7.0 |
| CVE-2026-21513 | MSHTML Framework Security Feature Bypass Vulnerability | Exploitation Detected | Yes | 8.8 |
| CVE-2023-2804 | Red Hat, Inc. CVE-2023-2804: Heap Based Overflow libjpeg-turbo | Exploitation Less Likely | No | 6.5 |
| CVE-2026-21236 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | Exploitation Unlikely | No | 7.8 |
| CVE-2026-21241 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | Exploitation More Likely | No | 7.0 |
| CVE-2026-21238 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | Exploitation More Likely | No | 7.8 |
| CVE-2026-21517 | Windows App for Mac Installer Elevation of Privilege Vulnerability | Exploitation Less Likely | No | 7.0 |
| CVE-2026-21234 | Windows Connected Devices Platform Service Elevation of Privilege Vulnerability | Exploitation Unlikely | No | 7.0 |
| CVE-2026-21246 | Windows Graphics Component Elevation of Privilege Vulnerability | Exploitation Unlikely | No | 7.8 |
| CVE-2026-21235 | Windows Graphics Component Elevation of Privilege Vulnerability | Exploitation Less Likely | No | 7.3 |
| CVE-2026-21250 | Windows HTTP.sys Elevation of Privilege Vulnerability | Exploitation Unlikely | No | 7.8 |
| CVE-2026-21240 | Windows HTTP.sys Elevation of Privilege Vulnerability | Exploitation Less Likely | No | 7.8 |
| CVE-2026-21232 | Windows HTTP.sys Elevation of Privilege Vulnerability | Exploitation Less Likely | No | 7.8 |
| CVE-2026-21248 | Windows Hyper-V Remote Code Execution Vulnerability | Exploitation Less Likely | No | 7.3 |
| CVE-2026-21247 | Windows Hyper-V Remote Code Execution Vulnerability | Exploitation Less Likely | No | 7.3 |
| CVE-2026-21244 | Windows Hyper-V Remote Code Execution Vulnerability | Exploitation Less Likely | No | 7.3 |
| CVE-2026-21255 | Windows Hyper-V Security Feature Bypass Vulnerability | Exploitation Less Likely | No | 8.8 |
| CVE-2026-21245 | Windows Kernel Elevation of Privilege Vulnerability | Exploitation Less Likely | No | 7.8 |
| CVE-2026-21239 | Windows Kernel Elevation of Privilege Vulnerability | Exploitation Less Likely | No | 7.8 |
| CVE-2026-21231 | Windows Kernel Elevation of Privilege Vulnerability | Exploitation More Likely | No | 7.8 |
| CVE-2026-21222 | Windows Kernel Information Disclosure Vulnerability | Exploitation Less Likely | No | 5.5 |
| CVE-2026-21243 | Windows Lightweight Directory Access Protocol (LDAP) Denial of Service Vulnerability | Exploitation Unlikely | No | 7.5 |
| CVE-2026-21249 | Windows NTLM Spoofing Vulnerability | Exploitation Less Likely | No | 3.3 |
| CVE-2026-21525 | Windows Remote Access Connection Manager Denial of Service Vulnerability | Exploitation Detected | No | 6.2 |
| CVE-2026-21533 | Windows Remote Desktop Services Elevation of Privilege Vulnerability | Exploitation Detected | No | 7.8 |
| CVE-2026-21510 | Windows Shell Security Feature Bypass Vulnerability | Exploitation Detected | Yes | 8.8 |
| CVE-2026-21508 | Windows Storage Elevation of Privilege Vulnerability | Exploitation Less Likely | No | 7.0 |
| CVE-2026-21242 | Windows Subsystem for Linux Elevation of Privilege Vulnerability | Exploitation Less Likely | No | 7.0 |
| CVE-2026-21237 | Windows Subsystem for Linux Elevation of Privilege Vulnerability | Exploitation Less Likely | No | 7.0 |
Zero-Day Vulnerabilities: Known Exploited
CVE | Title | Exploitation status | Publicly disclosed? | CVSS v3 base score |
|---|---|---|---|---|
| CVE-2026-21519 | Desktop Window Manager Elevation of Privilege Vulnerability | Exploitation Detected | No | 7.8 |
| CVE-2026-21514 | Microsoft Word Security Feature Bypass Vulnerability | Exploitation Detected | Yes | 7.8 |
| CVE-2026-21513 | MSHTML Framework Security Feature Bypass Vulnerability | Exploitation Detected | Yes | 8.8 |
| CVE-2026-21525 | Windows Remote Access Connection Manager Denial of Service Vulnerability | Exploitation Detected | No | 6.2 |
| CVE-2026-21533 | Windows Remote Desktop Services Elevation of Privilege Vulnerability | Exploitation Detected | No | 7.8 |
| CVE-2026-21510 | Windows Shell Security Feature Bypass Vulnerability | Exploitation Detected | Yes | 8.8 |
Critical Remote Code Execution/Elevation of Privilege
CVE | Title | Exploitation status | Publicly disclosed? | CVSS v3 base score |
|---|---|---|---|---|
| CVE-2026-21531 | Azure SDK for Python Remote Code Execution Vulnerability | Exploitation Less Likely | No | 9.8 |
Patch Tuesday - February 2026
Source: Rapid7
Source Link: https://www.rapid7.com/blog/post/em-patch-tuesday-february-2026