AI Hackathons and the Future of Security Architecture
Last week, a few Futurists met up to work out the practical realities of AI-enabled Red Teaming (among other topics). In addition to two days of phenomenal vibe coding in Cursor, the final presentations were light on hyperbole and heavy on capabilities and remarkable outcomes, created in a day or less. Two years ago, when LLMs made their mainstream debut, I was dubious, but the hackathon confirmed recent observations (last three months) that AI is accelerating security workflows (like everything else) at warp speed. Change, soon driven primarily through various agentic flavors, is happening at a pace that is difficult to comprehend.
The flight home was spent considering how to get ahead of the adversarial/defensive agent wars that will soon play out across the internet. Given the vast amount of uncertainty in agentic implementations and scale, there are no perfect solutions, but there are architecture scenarios worth considering NOW. Principal among them is IPv6. Long a headache for architects and engineers (nibble boundaries anyone?), IPv6 may now represent real business value through security, in exchange for the considerable effort. AI is a natural forcing function here. Given the time required to implement IPv6 and resolve the inevitable challenges along the way, enterprises should begin the work, aided by AI, of course.
Why IPv6 Belongs in Your Five-Year Security Roadmap
What if eliminating opportunistic attacks required nothing more than updating your network architecture? The vast IPv6 address space transforms internet-wide scanning from trivial to computationally impossible, removing one critical leg from the attacker's operational stool.
Modern adversaries operate on economics: maximum victims, minimum effort. IPv6's 340 undecillion addresses create an insurmountable barrier for brute-force discovery and enumeration, forcing attackers to abandon cheap, scalable tactics. Organizations dismissing this advantage miss a critical opportunity to reduce their attack surface while security teams fight multi-front battles against AI-powered threats.
The Opportunistic Threat Reality
Recorded Future tracks thousands of automated exploitation campaigns daily, following a predictable pattern. Vulnerability disclosure triggers mass scanning within hours, leading to indiscriminate compromise of exposed systems.
Recent campaigns demonstrate the scale:
- CVE-2025-31324 (SAP NetWeaver): 581 systems compromised via mass scanning; 1,800+ targets identified
- CVE-2024-3400 (PAN-OS): thousands of compromised devices in 72 hours
- CVE-2023-4966 (CitrixBleed): Over 20,000 servers breached via automated scanning
- CVE-2023-34362 (MOVEit Transfer): 2500 instances exposed to the internet; initial access through internet-wide vulnerability discovery
The volume metrics paint a sobering picture. IoT devices are attacked within 5 minutes of connecting to the internet. Internet background noise includes 4.2 billion simultaneous events (five years ago). 152 billion scan probes are sent across the IPv4 internet daily, including 36,000 automated scans per second.
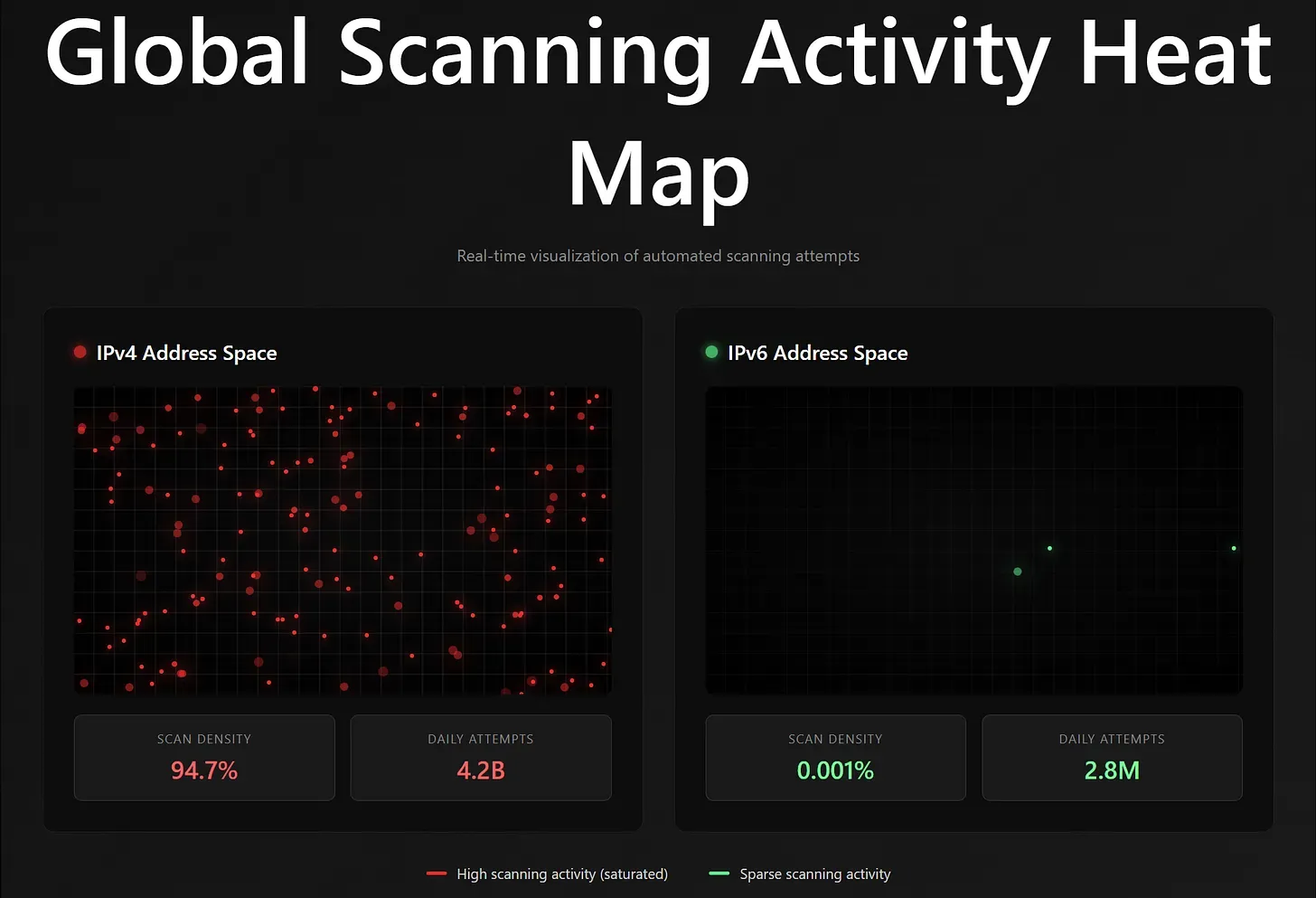 Claude Sonnet 4 render of IPv6 vs. IPv4 scanning.
Claude Sonnet 4 render of IPv6 vs. IPv4 scanning.
[Dynamic Visualization: Global Scanning Heat Map - AI render showing IPv4 saturation]
The Three-Legged Stool of Modern Remote Attacks
Threat actors balance operations on three critical foundations. Remove any leg, and its operational efficiency collapses.
Leg Alpha: Opportunistic Scanning Automated discovery exploits internet-exposed vulnerabilities at scale. IPv6 effectively saws off this leg by making comprehensive scanning computationally infeasible.
Leg Beta: Targeted Reconnaissance Domain enumeration, supply chain analysis, and social engineering remain unaffected. Adversaries leverage Certificate Transparency logs, passive DNS, and BGP announcements to build targeted hit lists.
Leg Charlie: Identity & Insider Access Compromised credentials and third party breaches bypass network controls entirely. Address space complexity offers zero defense against authenticated attacks (and social engineering, which is a fourth leg).
Reality Check: IPv6 Security Benefits
The security community debates IPv6's defensive value, but data supports nuanced conclusions. Brute-force scanning genuinely becomes hardereven the fastest academic scanners map only millions of hosts from 2^128 possibilities.
However, targeted discovery remains trivial. Adversaries enumerate targets through domain names, WHOIS records, and Certificate Transparency logs. Dual-stack deployments particularly undermine benefits, as attackers simply pivot from IPv4 reconnaissance.
Key defensive advantages include:
- Address space enables thousands of deception nodes
- Granular segmentation without NAT complexity
- Protocol modernization enforces TLS 1.3 and QUIC
- Moving-target defense becomes economically viable
Practical Implementation Architecture
Organizations should maximize IPv6's defensive advantages while acknowledging its limitations. The evidence-based approach spans three phases over 24 months.
Phase Alpha: Foundation (Months 0-6) Deploy dual-stack architecture with IPv6-preferred public services. Implement strict ICMPv6 filtering, unpredictable address allocation, and comprehensive connection monitoring. Every IPv6 probe becomes a high-value threat signal.
Phase Beta: Segmentation (Months 6-12) Allocate /64 subnets per application tier with host-based microsegmentation. Deploy source address validation at edge routers and create honeypot networks throughout unused address space.
Phase Gamma: Advanced Defense (Months 12-24) Enable rapid address rotation for moving-target defense. Deploy IPv6-only management interfaces behind Single Packet Authorization, integrate telemetry into threat-hunting platforms, and participate in collaborative intelligence sharing.
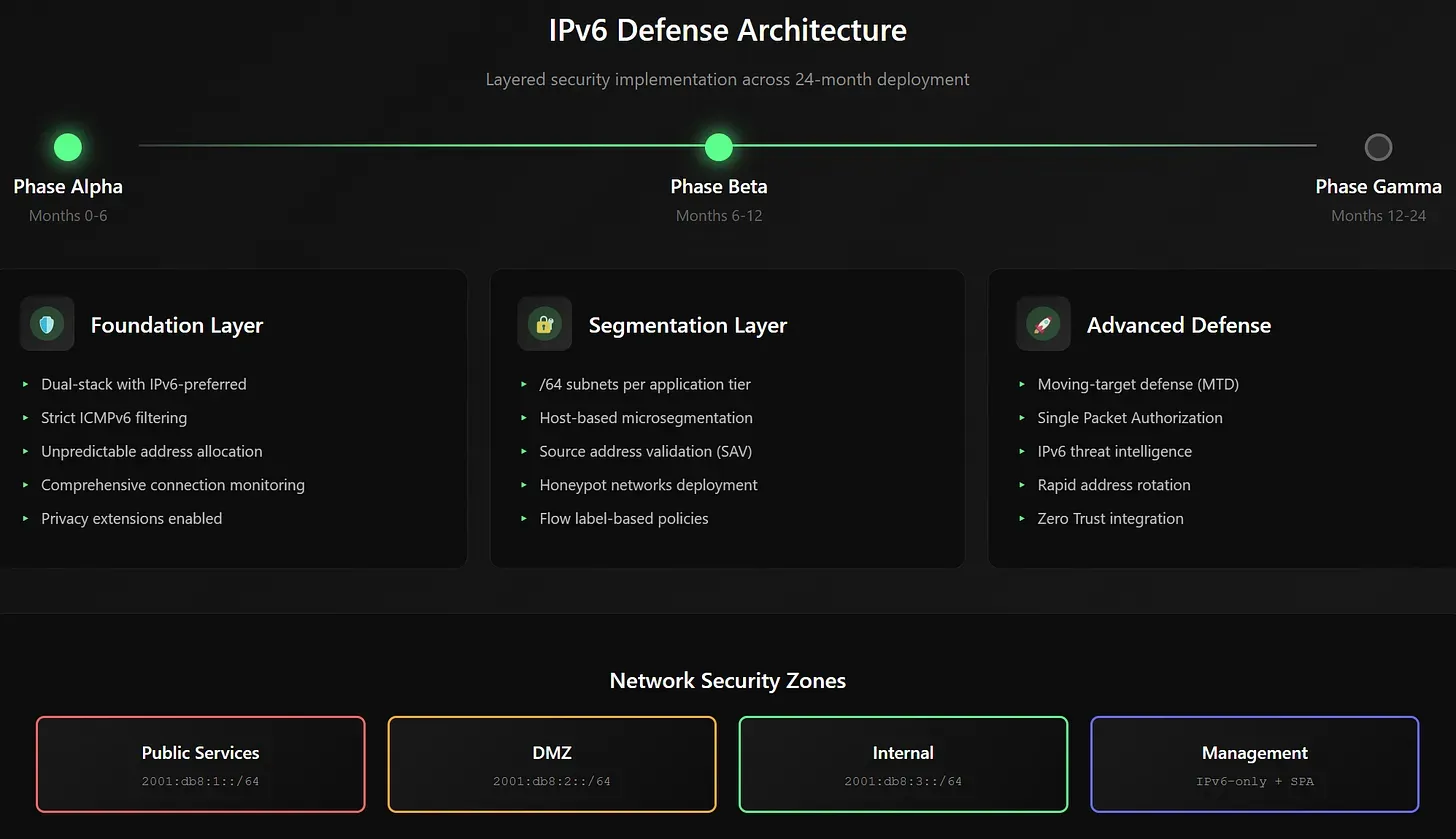 Claude Sonnet 4 generated IPv6 implementation timeline.
Claude Sonnet 4 generated IPv6 implementation timeline.
[Dynamic Visualization: IPv6 Defense Architecture - AI render]
Measuring Risk Reduction
IPv6 deployment will deliver a significant drop in scanning, and additional canary hosts/services will help create metrics that translate to increased operational efficiency. Security teams spend less time chasing automated noise, focusing instead on sophisticated threats that matter.
Future-Proofing Against AI-Powered Attacks
The next five years demand strategies that counter automated exploitation at machine speed. IPv6 enables several critical defensive patterns that become essential as AI agents weaponize vulnerabilities within minutes.
Autonomous Defense Pipelines: Integrate CVE feeds with LLM agents that generate patches faster than attackers can weaponize exploits. Deploy eBPF-based sidecars ingesting real-time signatures, pushing rules globally via service mesh.
Zero-Exposure Architecture: Hide services behind cryptographic authentication using Single Packet Authorization or modern ZTNA. Removes targets from the attack graph entirelyzero exposed surface equals zero remote exploitation (in theory).
Continuous Surface Mutation: Leverage abundant IPv6 space for constant re-addressing and port shuffling. Combined with binary diversification and container re-imaging, force adversaries to continuously rediscover targets.
Strategic Recommendations
Security leaders planning 2025-2030 roadmaps should consider adopting this blueprint:
- Deploy IPv6-only for public services where feasible
- Publish no AAAA DNS records for management interfaces
- Automate defensive kill-chains matching attacker speed
- Implement moving-target techniques using address abundance
- Shift to memory-safe languages, eliminating bug classes
- Treat every /64 scan as suspicious intelligence
- Share sanitized samples with collaborative defense communities
The Bottom Line
IPv6 won't stop nation-states or targeted ransomware groups, but it eliminates the background radiation consuming security resources. Opportunistic campaigns that compromise thousands of organizations simply cannot operate efficiently in IPv6's vast address space.
Smart organizations recognize that removing entire attack classes beats chasing perfect security. IPv6 takes mass scanning off the table, forcing adversaries to reveal themselves through targeted activity. In an era where defensive teams need every advantage, that's one less leg supporting the attacker's operational modeland one more reason IPv6 belongs in your security roadmap.
 Claude Sonnet 4 generated IPv6 cube.
Claude Sonnet 4 generated IPv6 cube.
Source: RecordedFuture
Source Link: https://www.recordedfuture.com/blog/ipv6-drip-drowns-spray-and-pray