Globally, regulations and directives are significantly altering the way organizations address cyber resilience, emphasizing the necessity for a more proactive stance. This is evident in both the Digital Operational Resilience Act (DORA) and the second version of the Network and Information Systems Directive (NIS2).
What is DORA?
DORA establishes technical standards for EU member states to adopt as it relates to covered entities and their critical third-party Information & Communications Technology (ICT) providers across EU member states. ICT is considered to be so influential and essential to economic development and business growth that it has been credited with ushering in the Fourth Industrial Revolution. However, this reliance on ICT means that organizations must focus on digital resilience to minimize risk of not being able to deliver critical and important services.
Who Does DORA Apply To?
The measures detailed by DORA will be applicable to both traditional and non-traditional financial entities operating in the EU and their ICT providers. ICT is broad and covers tools like cloud computing, software, hardware, transactions, communications, data, internet access, and more.
Why is DORA Being Implemented?
The increasing reliance on digital technologies in the financial sector has been heard loud and clear - thus DORA was proposed. DORA aims to make sure that financial institutions can withstand, respond to, and recover from ICT-related disruptions and threats. Ultimately the Act aims to elevate the operational resilience of financial entities, safeguard financial stability, and protect consumers from the adverse impacts of digital disruptions.
Impact of Cyber Attacks on Financial Sector
The financial sector saw a dramatic increase in Distributed Denial of Service (DDoS) attacks, with a 154% rise from 2022 to 2023. In EMEA (Europe, Middle East, and Africa) the financial services sector accounted for 66% of all DDoS attacks, compared with 28% in North America. This surge in DDoS attacks against EMEA financial services institutions is likely due to geopolitical tensions and hacktivist activities related to the Russia-Ukraine conflict, making the financial sector the most targeted by these types of attacks. (FS ISAC)
Though not specifically against the Financial Sector, the MOVEit transfer attack highlights the impact of ICT. In 2023, a ransomware group named CL0P exploited a zero-day vulnerability in MOVEit, a managed file transfer software. This attack affected multiple organizations, including financial institutions and healthcare providers. CL0Ps MOVEit campaign garnered upwards of $100M in profit for the group, impacting over 2,750 organizations and 94 million individuals. It highlights the far-reaching impact software supply chain attacks can have.
Pillars of DORA
- ICT Risk Management and Governance: DORA will seek to mandate that the managing body of an organization holds ultimate responsibility for overseeing ICT risk. It emphasizes the need for a well-documented ICT risk management framework to swiftly, efficiently, and comprehensively tackle both cyber and physical risks.
- Incident Response and Reporting: Organizations will be required to maintain documented systems for monitoring, managing, logging, classifying, and reporting ICT-related incidents. This ensures prompt and effective responses to any issues that arise.
- Digital Operational Resilience Testing: Financial institutions under DORA must regularly test their defenses and identify any vulnerabilities in their ICT systems. This proactive approach helps maintain robust protections against potential threats.
- Third-Party Risk Management: DORA seeks to impose requirements not only for financial institutions, but also for their ICT providers. Critical ICT third-party service providers are often subject to oversight from relevant managing bodies. Financial firms should actively manage ICT third-party risks through contractual agreements and diligent oversight, ensuring a comprehensive risk management strategy to ensure compliance.
What is NIS2?
NIS2 aims to improve the cybersecurity capabilities across the EU by ensuring a high common level of cybersecurity across member states. NIS2 expands on the previous directive by addressing some gaps and shortcomings identified over the past few years.
Key Changes Introduced by NIS2
NIS2 introduces several significant changes aimed at enhancing cybersecurity measures and ensuring a more uniform implementation across the EU. Some of the key changes include:
- Broader Scope: NIS2 extends its coverage to more sectors, including public administration, space, manufacturing of critical products, and food supply chains, reflecting the evolving landscape of digital threats.
- Stricter Security Requirements: The directive sets higher standards for cybersecurity risk management measures, incident reporting, and supply chain security. Organizations may need to implement a range of technical and organizational measures to protect their networks and information systems.
- Enhanced Cooperation and Information Sharing: NIS2 promotes greater cooperation between member states and encourages information sharing among public and private entities to improve the overall security posture.
- Incident Reporting: Organizations are required to report significant incidents to relevant authorities within 24 hours, ensuring a swift response to potential threats.
Areas of Focus for Organizations
Both DORA and NIS2 highlight the importance of risk management, supply chain security, and development and maintenance of robust incident response plans. In order to adapt to these requirements, there are some key areas for businesses to focus on:
Implementing both proactive and reactive processes towards mitigating risk
Implementing both proactive and reactive processes towards mitigating risk is crucial for true cyber resilience. Proactive measures, such as regular risk assessments, vulnerability scans, and the deployment of security controls, enable organizations to anticipate and prevent potential threats before they materialize. This forward-thinking approach helps to fortify an organizations defenses, ensuring that they are resilient against emerging cyber threats. On the other hand, reactive processes, including incident response plans, real-time monitoring, and forensic investigations, can be essential for addressing and mitigating the impact of security incidents when they occur.
Focusing on your third-party suppliers as a part of your organizations attack surface
Third-party vendors are a critical component to todays modern business, helping to accelerate product deliveries, spur innovation, increase efficiency, and lower average costs. The average company shares confidential information with 583 parties, according to a Ponemon Institute study. Its no surprise why Gartner estimates that by 2025 nearly half of organizations worldwide will have experienced attacks on their software supply chains, a three-fold increase from 2021.
The challenge is that more than 2/3 of organizations have a limited, ad hoc understanding, or none at all of their third and fourth party risk.
Traditionally the primary mechanism for managing down cyber supply chain risk has been through preventative measures: due diligence reviews, lengthy questionnaires, and extensive back and forth communication. These efforts are a blanket approach that is cumbersome, lacks scalability, and is difficult to enforce. Prevention is always an admirable pursuit, but detection is critical, especially in an increasingly connected world. Read more about Supply Chain Resilience & the Power of Continuous Monitoring in our blog post.
Streamlined processes for incident response
As part of the DORA framework, there may be some organizations that may be required to submit an initial notification in as little as 4 hours of an incident being classified as major. These strict timelines mean a streamlined incident response process is critical, getting information into the hands of analysts as quickly as possible.
Under NIS2, organizations may be required to submit an early warning within 24 hours of any significant incident and a full notification report within 72 hours, which needs to include the assessment of the incident, severity and impact, and related IOCs. In this case, getting information into the hands of the analysts as quickly as possible is critical.
How Threat Intelligence Can Help
Gain a complete view of your threat landscape to identify what matters to you
- Quickly identify top threat actors of interest, especially targeting your third-parties
- Determine most concerning malware based on your companys technologies
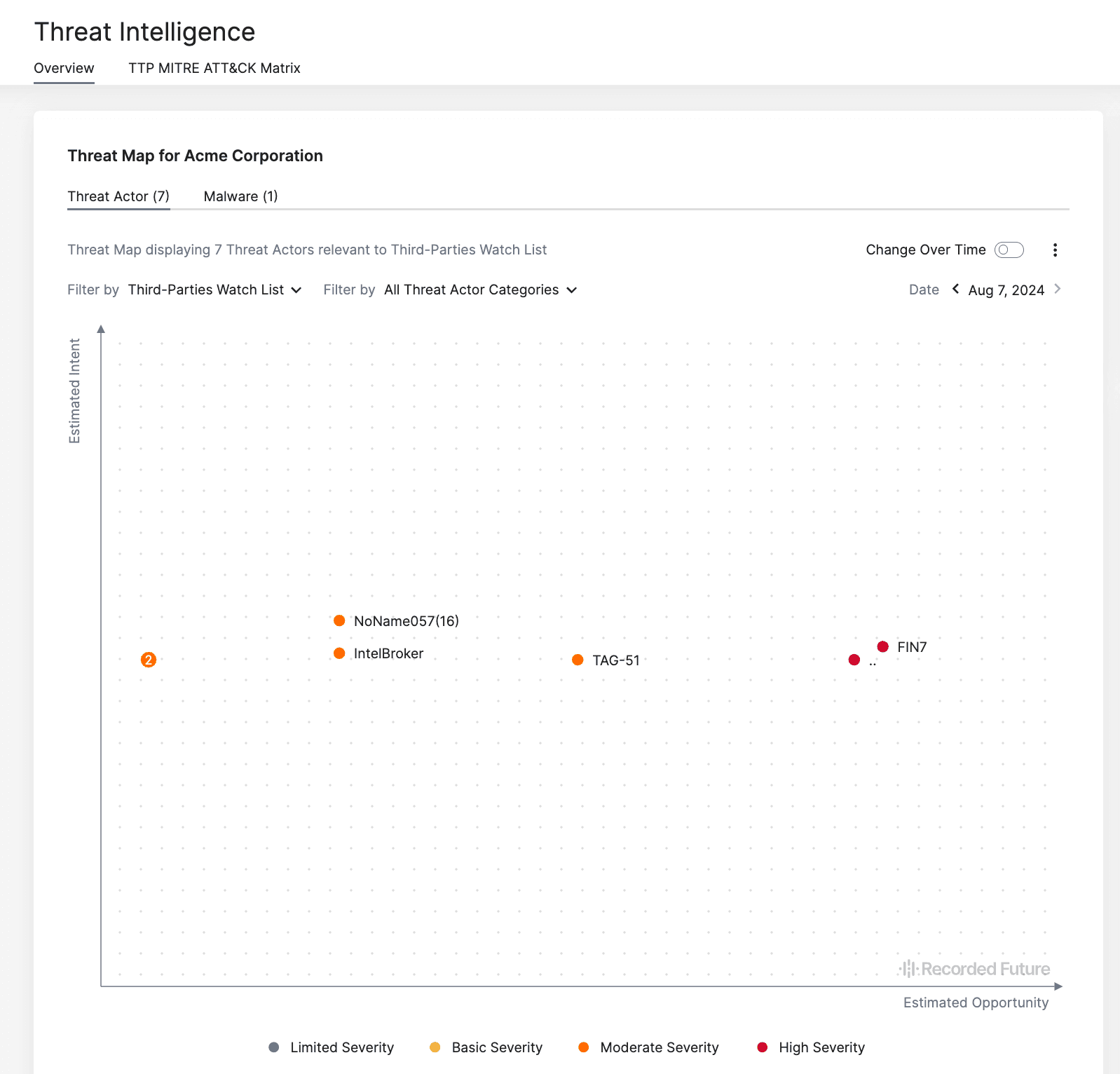
Implement security controls and make adjustments as necessary
- Understand the technical parameters of malware used in threat actor campaigns to close specific ports
- Update block lists with continuously validated IP addresses and domains for command & control (C2), botnet and remote access trojan (RAT) infrastructure
- Automatically reset passwords in an identity access management (IAM) system with recently stolen credentials
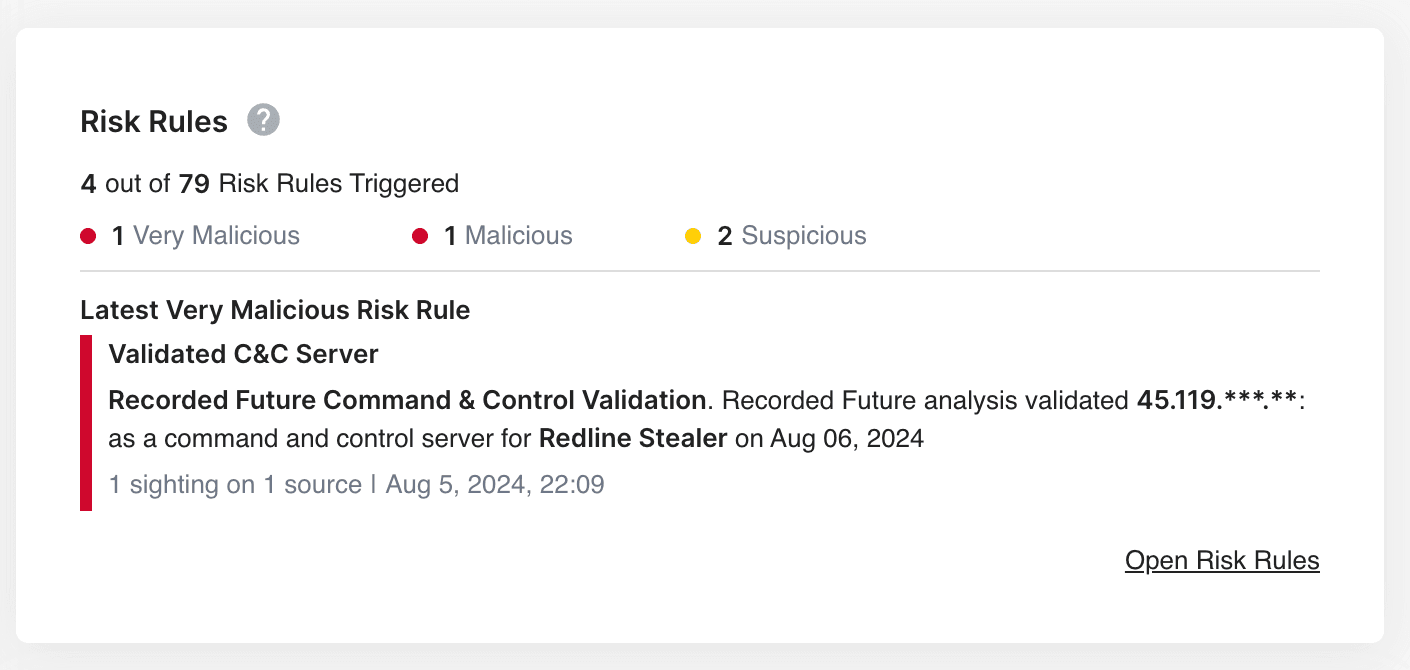
Mitigate software threats originating from 3rd and 4th party vendors
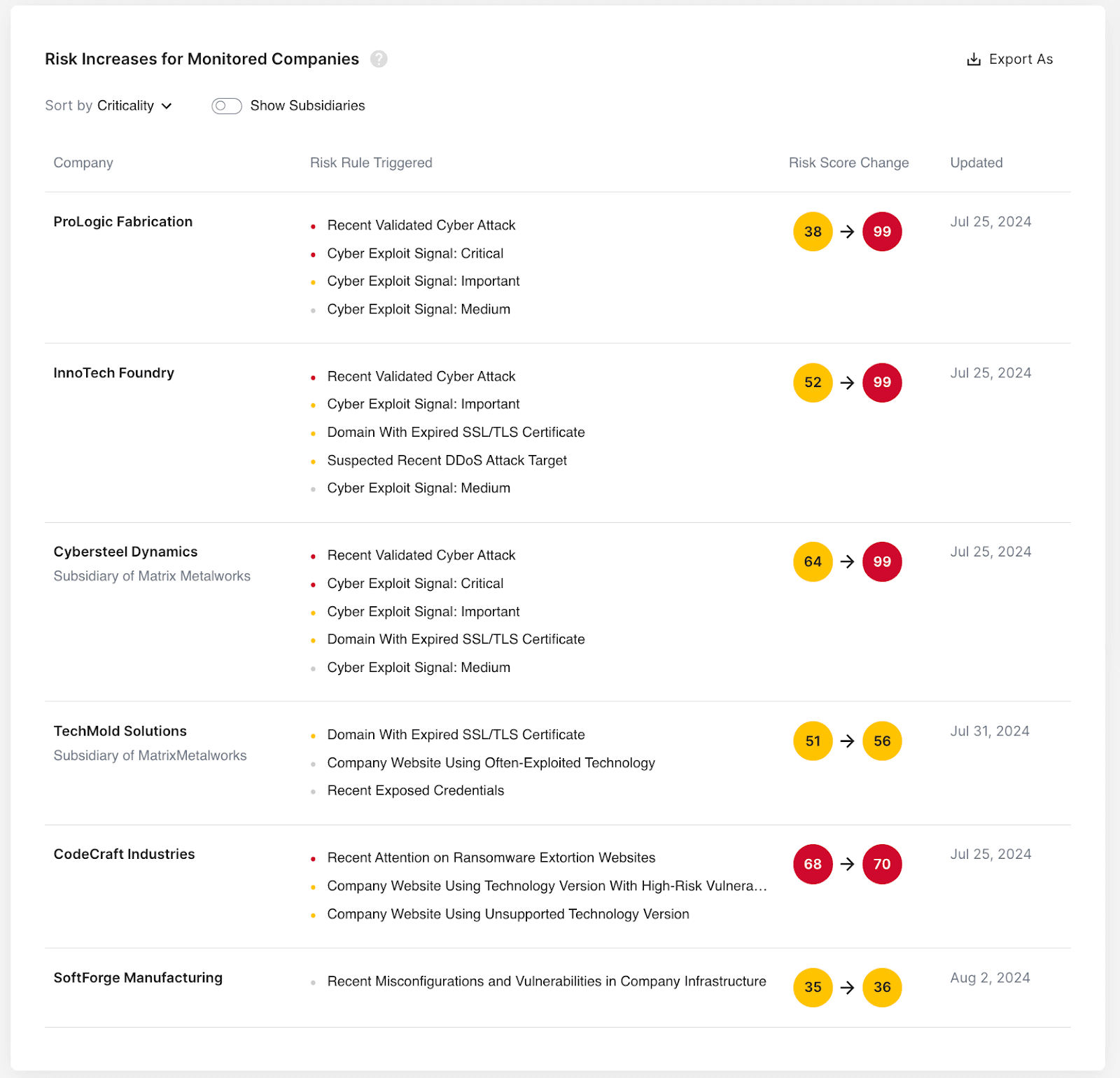
- Enrich vulnerabilities on scanned third-party products with data on weaponization
- Dynamic risk scoring for third-parties, updated in real-time
Detect new threats with context
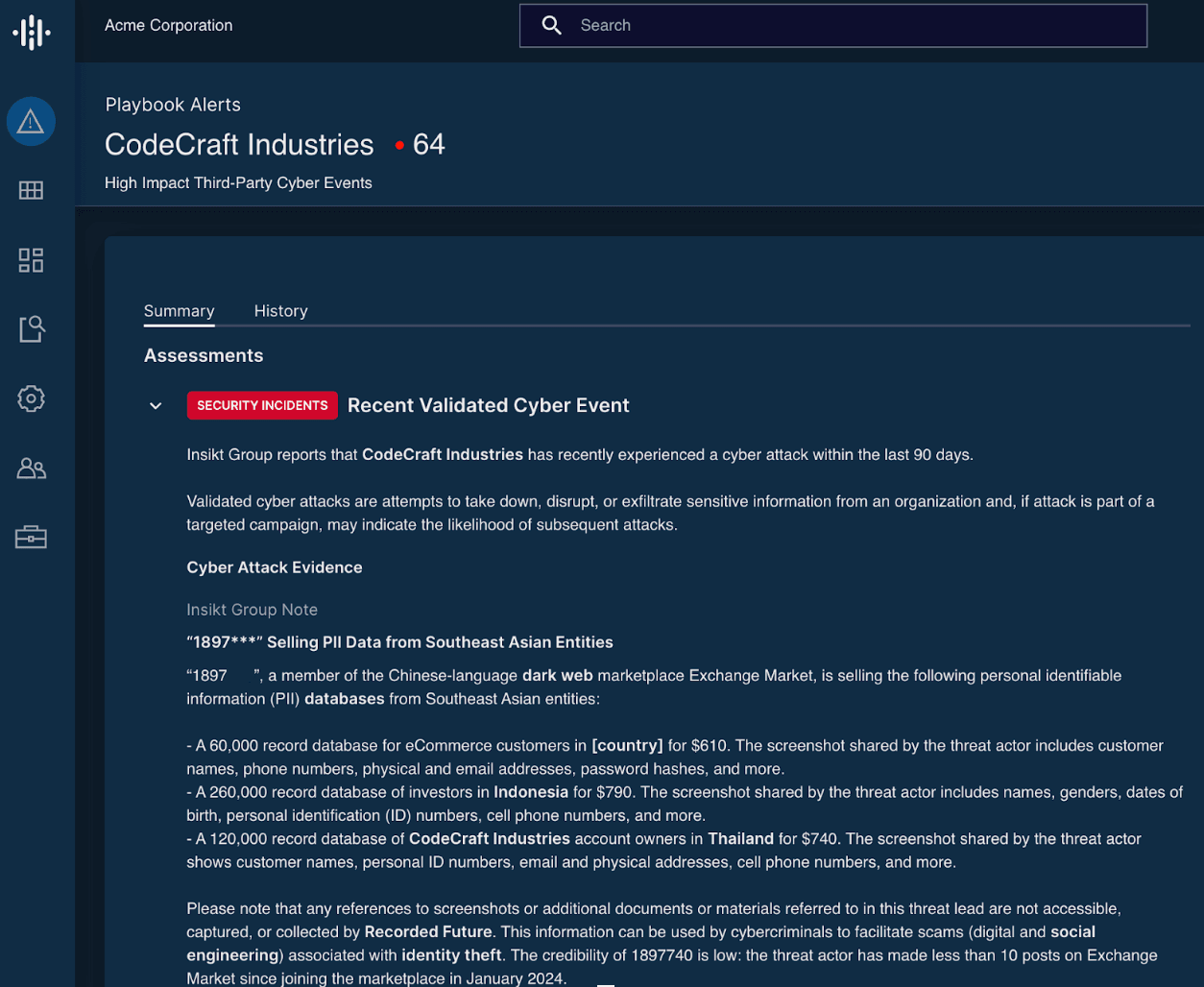
- Receive a notification within minutes of a potential breach impacting a key third-party, such as a database offered for sale
- Detect references to your brand and secret keywords on ransomware extortion sites to quickly understand the severity of potential leaked documents
Decrease time to respond and report
- Equip users with essential information, updated in real time, on their threat landscape
- Reduce time spent searching, summarizing, and writing reports by hours
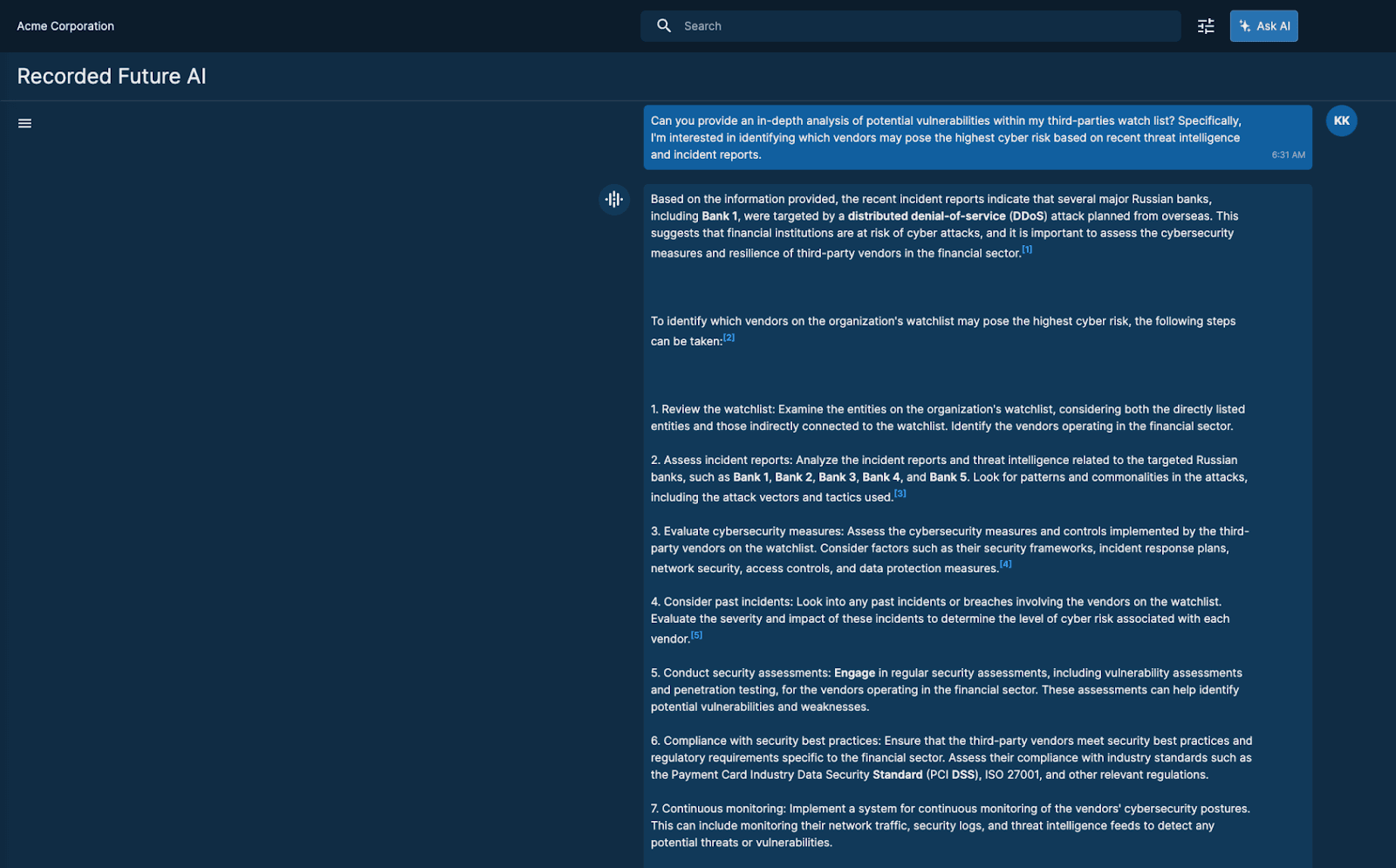
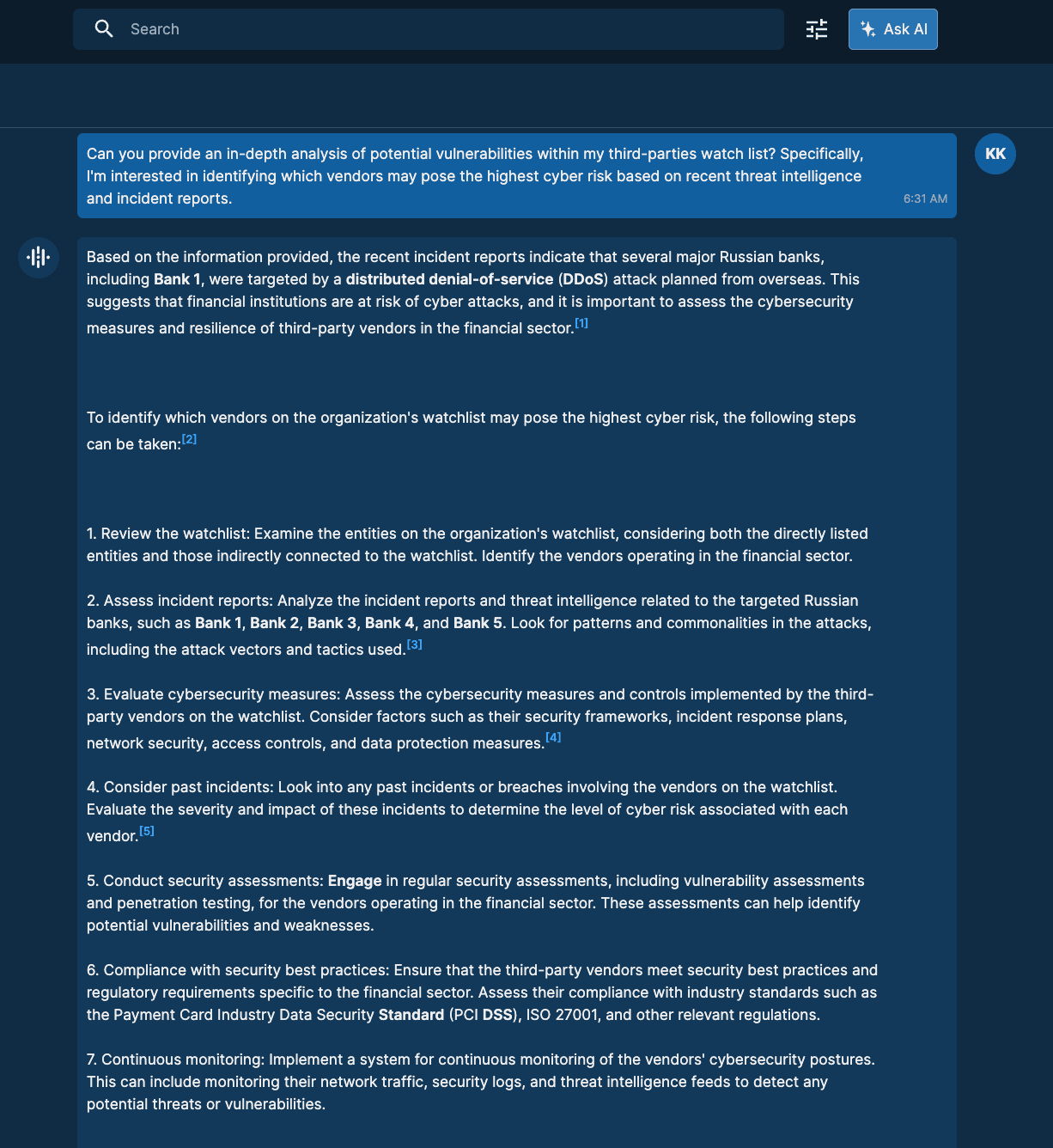
- Recorded Future AI answers your questions about threat patterns, implications, and intelligence sources
A Cyber-Resilient Future
Risk management, supply chain security, and incident response are pivotal components of DORA, each playing a crucial role in strengthening an organizations cybersecurity framework. When organizations are able to integrate threat intelligence into our broader strategy, they are able to be truly proactive - understanding who may be targeting us and why, identify gaps in current programs, understand what investments need to be made, and build on strong foundations with new capabilities. Especially when it comes to directives like DORA where there may be a certain degree of flexibility in exactly how to meet requirements, organizations need to put in place processes that are flexible and scalable to meet regulation requirements of today and those that may be seen in the future.
Source: RecordedFuture
Source Link: https://www.recordedfuture.com/blog/dora-regulation-cyber-resilience-eu