‘Last Mile Reassembly Attacks’ evade every Secure Web Gateway in the market and deliver known malware to the endpoint
At DEF CON 32, SquareX presented groundbreaking research curating vulnerabilities in Secure Web Gateways (SWGs) that leave organizations vulnerable to threats that these tools fail to detect. These traditional defenses, once considered the gold standard for enterprise security, can now be easily bypassed through client-side web attacks that they simply cannot protect against. Collectively, these attacks are called ‘Last Mile Reassembly Attacks’.
WebAssembly, a boon and a bane
Among the most concerning of these threats is the use of WebAssembly (WASM), a powerful web technology that can deliver malware directly to a user’s browser, evading SWG detection entirely. This binary instruction format allows high-performance execution of code in web browsers, enabling complex applications to run with near-native speed. However, its power and flexibility also make it an attractive vector for cyberattacks, particularly in environments where Secure Web Gateways (SWGs) are the primary line of defense.
WebAssembly is designed to work alongside JavaScript, allowing developers to execute code with higher efficiency and performance. It’s widely adopted by organizations to enhance web applications. SWGs, which are traditionally focused on inspecting network traffic at the layer of HTML, CSS, and JavaScript, are often blind to the intricacies of WebAssembly modules.
The problem lies in the fact that SWGs, operating at the network layer, do not perform the necessary dynamic analysis on WebAssembly code. This lack of visibility means that malicious actors can embed malware within WASM modules, which can then be extracted directly on the browser, bypassing the SWG’s detection mechanisms entirely.
For instance, an attacker could conceal malicious payloads within a WebAssembly module and distribute it through a compromised or even a legitimate website. Since SWGs lack the capability to analyze WebAssembly files, the malicious content slips through the network defenses undetected. The malware is assembled on the client-side and downloaded to the victim’s endpoint.
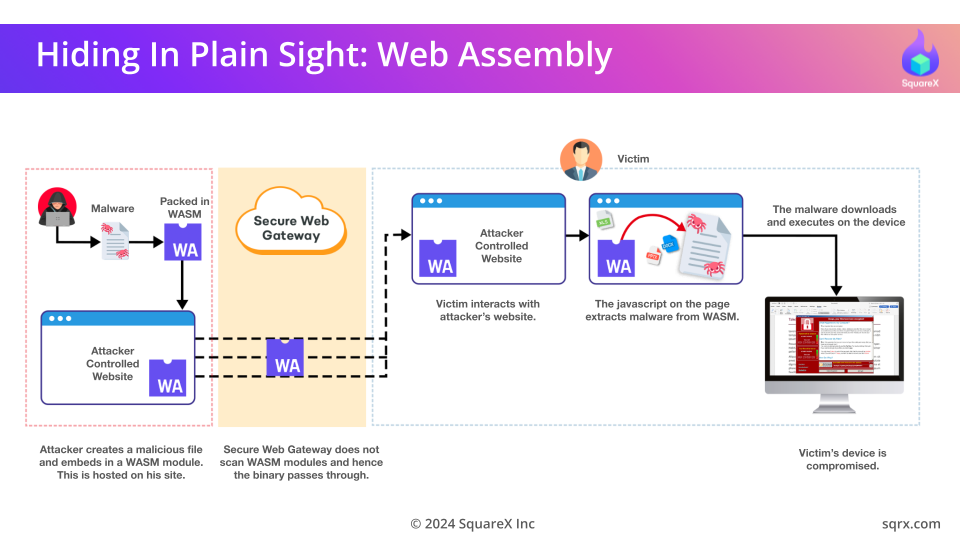
This threat is exacerbated by the fact that there is currently a lack of industry-standard security frameworks specifically designed to analyze and protect against malicious WebAssembly code. As a result, many enterprises remain vulnerable to this method of attack, relying on outdated SWGs that were never designed to handle such complex threats.
The need for a browser-native security approach
The implications of this vulnerability are clear: enterprises can no longer depend solely on network-layer defenses like SWGs to protect against the full spectrum of modern web threats. A more effective approach involves adopting browser-native security solutions, which operate directly within the browser and can analyze WebAssembly modules in real-time. These solutions provide the necessary visibility and control to detect and neutralize threats before they can cause damage.
As WebAssembly continues to gain traction in the development of web applications, enterprises must recognize the limitations Secure Web Gateways and take proactive steps to protect their environments with solutions designed to handle the complexities of today’s web technologies.
Assess your Secure Web Gateway
Similar to smuggling malware through WebAssembly modules, there are more than 30 attacks that bypass all Secure Web Gateways. Check if your enterprise is vulnerable to them at https://browser.security/

WebAssembly: The Fly on the Wall Delivering Malware Past Secure Web Gateways was originally published in SquareX Labs on Medium, where people are continuing the conversation by highlighting and responding to this story.
The post WebAssembly: The Fly on the Wall Delivering Malware Past Secure Web Gateways appeared first on Security Boulevard.
Engineering @ SquareX
Source: Security Boulevard
Source Link: https://securityboulevard.com/2024/08/webassembly-the-fly-on-the-wall-delivering-malware-past-secure-web-gateways/